Fluffy - Hack The Box

 The Fluffy machine is a Windows machine that involves Active Directory enumeration. We’ll exploit Kerberos and other misconfigurations to gain domain administrator privileges.
The Fluffy machine is a Windows machine that involves Active Directory enumeration. We’ll exploit Kerberos and other misconfigurations to gain domain administrator privileges.

 The Fluffy machine is a Windows machine that involves Active Directory enumeration. We’ll exploit Kerberos and other misconfigurations to gain domain administrator privileges.
The Fluffy machine is a Windows machine that involves Active Directory enumeration. We’ll exploit Kerberos and other misconfigurations to gain domain administrator privileges.
 We developed a joint adversarial attack that combines image and text perturbations to bypass the safety filters of advanced Vision-Language Models (VLMs) like LLaVA and Gemma.
We developed a joint adversarial attack that combines image and text perturbations to bypass the safety filters of advanced Vision-Language Models (VLMs) like LLaVA and Gemma.

 Exploring Active Directory vulnerabilities to achieve domain administrator access.
Exploring Active Directory vulnerabilities to achieve domain administrator access.

 The blurry machine shows a vulnerability in ClearML, a development suite for ML/DL. It is classified with a medium difficulty.
The blurry machine shows a vulnerability in ClearML, a development suite for ML/DL. It is classified with a medium difficulty.

 The Drive machine is a hard Linux system that needs reverse engineering, and performing a SQL injection on a binary.
The Drive machine is a hard Linux system that needs reverse engineering, and performing a SQL injection on a binary.
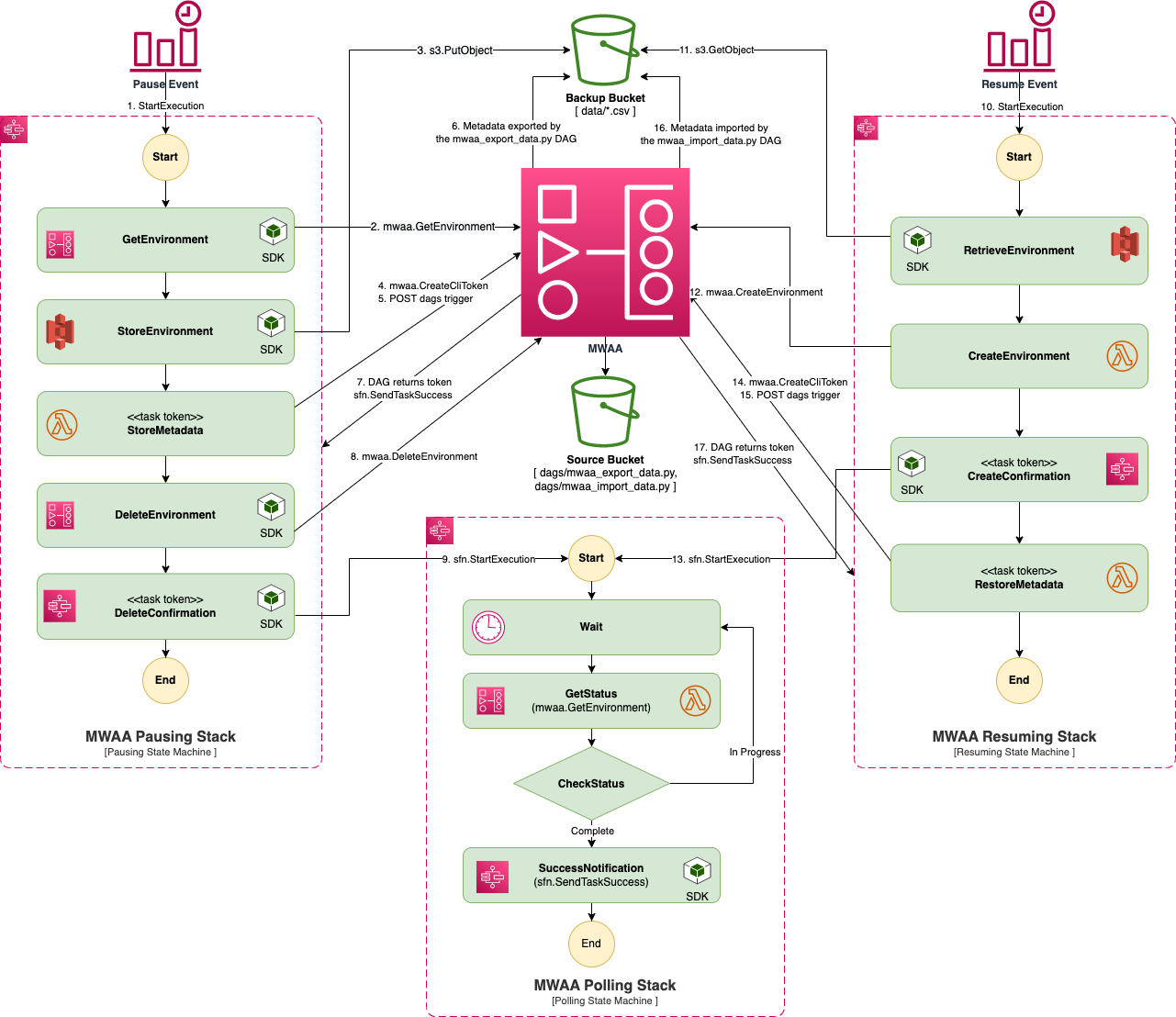 Optimizing ETL processes using a serverless architecture with Apache Airflow on AWS MWAA, achieving significant cost savings and efficiency.
Optimizing ETL processes using a serverless architecture with Apache Airflow on AWS MWAA, achieving significant cost savings and efficiency.

 Análisis forense de un volcado de memoria volátil (RAM) utilizando Volatility
Análisis forense de un volcado de memoria volátil (RAM) utilizando Volatility

 Configuración y personalización de un entorno Linux orientado a pruebas de penetración y seguridad ofensiva
Configuración y personalización de un entorno Linux orientado a pruebas de penetración y seguridad ofensiva

 This system is exploited, after some fuzzing, through a Tomcat manager with path traversal that makes the typical WAR shell a bit more difficult, and lateral movement is performed, as well as privilege escalation, through ansible misconfigurations.
This system is exploited, after some fuzzing, through a Tomcat manager with path traversal that makes the typical WAR shell a bit more difficult, and lateral movement is performed, as well as privilege escalation, through ansible misconfigurations.

 Spider is a complex machine with two SSTI vulnerabilities, and a really interesting method to get cookies with its private key. To escalate privileges we take advantage of the fact that we are allowed to enter input in an XML file, of which a parameter is displayed in a web service.
Spider is a complex machine with two SSTI vulnerabilities, and a really interesting method to get cookies with its private key. To escalate privileges we take advantage of the fact that we are allowed to enter input in an XML file, of which a parameter is displayed in a web service.

 Dynstr is a different box that works with dynamic dns and a really uncommon privilege escalation. It is not an OSCP style box, but it is also interesting because of how different it is. We can learn many things about DNS with this system.
Dynstr is a different box that works with dynamic dns and a really uncommon privilege escalation. It is not an OSCP style box, but it is also interesting because of how different it is. We can learn many things about DNS with this system.

 Monitors is a hard machine that goes from apache, cacti, to wordpress servers. Privilege escalation involves lateral movement between users and escaping from a docker image, which makes this machine a long and difficult challenge, but very entertaining for somewhat experienced attackers.
Monitors is a hard machine that goes from apache, cacti, to wordpress servers. Privilege escalation involves lateral movement between users and escaping from a docker image, which makes this machine a long and difficult challenge, but very entertaining for somewhat experienced attackers.

 Cap is one of the easiest Linux machines available in the platform. It is the machine that I always recommend to my degree partners that want to start in HackTheBox, as it is very intuitive and the required tools are known for every person with IT knowledges, even if it is their first machine.
Cap is one of the easiest Linux machines available in the platform. It is the machine that I always recommend to my degree partners that want to start in HackTheBox, as it is very intuitive and the required tools are known for every person with IT knowledges, even if it is their first machine.

 Pit is a medium HackTheBox machine that targets SNMP exploitation and enumeration. It is enumerated with the public community, and an attack to SeedDMS gives us RCE to gain access to a CentOS control pannel. Some misconfigurations in a bash script which works with SNMP are used to escalate privileges and root this quite complex system.
Pit is a medium HackTheBox machine that targets SNMP exploitation and enumeration. It is enumerated with the public community, and an attack to SeedDMS gives us RCE to gain access to a CentOS control pannel. Some misconfigurations in a bash script which works with SNMP are used to escalate privileges and root this quite complex system.

 The Schooled HackTheBox machine is a Medium FreeBSD system with a Moodle web content manager, very real-life applicable as many school and university systems are configured the same way as this one. From a simple school webpage, you go through student, teacher and manager accounts to finally root the system.
The Schooled HackTheBox machine is a Medium FreeBSD system with a Moodle web content manager, very real-life applicable as many school and university systems are configured the same way as this one. From a simple school webpage, you go through student, teacher and manager accounts to finally root the system.

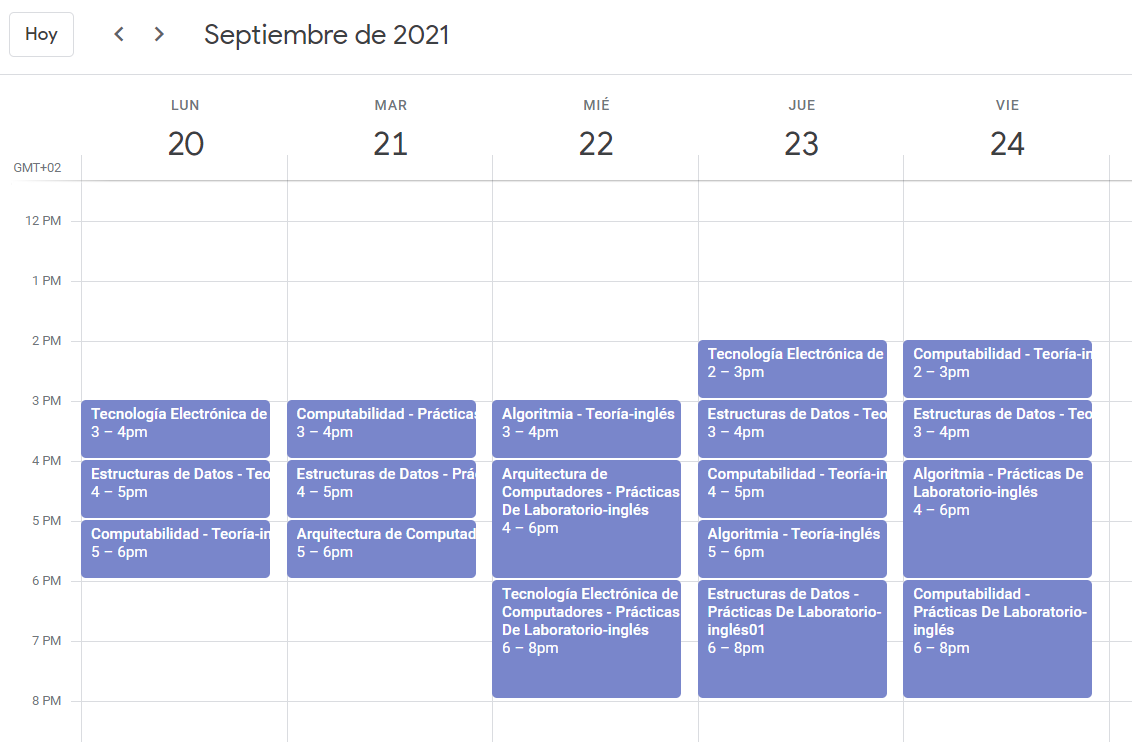 autoUniCalendar is a script which converts the Uniovi calendar into Google and Microsoft calendars by reading the HTTP requests to the web server, and parsing the calendar data into a CSV file readable by every calendar application.
autoUniCalendar is a script which converts the Uniovi calendar into Google and Microsoft calendars by reading the HTTP requests to the web server, and parsing the calendar data into a CSV file readable by every calendar application.

 The Knife machine of HackTheBox is an easy Linux machine very useful to understand basic concepts about enumeration, and how to stablish a simple reverse shell. It is also helpful to understand the escalation of privileges using GTFObins.
The Knife machine of HackTheBox is an easy Linux machine very useful to understand basic concepts about enumeration, and how to stablish a simple reverse shell. It is also helpful to understand the escalation of privileges using GTFObins.

 Love is a very easy Windows machine that can be easily solved if some basic concepts are clear. It contains a SSRF attack, which is not very common, and this machine is a very good example of how it works. Enumeration is also very important here, for both foothold and privilege escalation, this last one taking advantage of the AlwaysInstallElevated feature being turned on.
Love is a very easy Windows machine that can be easily solved if some basic concepts are clear. It contains a SSRF attack, which is not very common, and this machine is a very good example of how it works. Enumeration is also very important here, for both foothold and privilege escalation, this last one taking advantage of the AlwaysInstallElevated feature being turned on.

 Tabby is an easy and enjoyable Linux machine with an LFI to get the foothold, user pivoting from tomcat and an abuse of the lxd group privilege.
Tabby is an easy and enjoyable Linux machine with an LFI to get the foothold, user pivoting from tomcat and an abuse of the lxd group privilege.

 Remote is a Windows machine with the Umbraco web content manager, which is exploited through a mountable partition and cached credentials whose greatest vulnerability is an outdated version of Umbraco, what makes possible to exploit the machine.
Remote is a Windows machine with the Umbraco web content manager, which is exploited through a mountable partition and cached credentials whose greatest vulnerability is an outdated version of Umbraco, what makes possible to exploit the machine.

 Sauna is a very complete Windows machine, in which some of the most common tools are used to gain access and escalate privileges in the system. The enumeration requires making a list of possible usernames using the about page of the website. In the privilege escalation, the Pass-The-Hash technique is used to become administrator, which makes the machine interesting at the same time that it is easy and enjoyable to start with Windows pentesting.
Sauna is a very complete Windows machine, in which some of the most common tools are used to gain access and escalate privileges in the system. The enumeration requires making a list of possible usernames using the about page of the website. In the privilege escalation, the Pass-The-Hash technique is used to become administrator, which makes the machine interesting at the same time that it is easy and enjoyable to start with Windows pentesting.